-
Notifications
You must be signed in to change notification settings - Fork 14
Regsvcs Regasm
Regsvcs and Regasm are Windows command-line utilities that are used to register .NET Component Object Model (COM) assemblies. Both are digitally signed by Microsoft. Adversaries can use Regsvcs and Regasm to proxy execution of code through a trusted Windows utility. Both utilities may be used to bypass process whitelisting through use of attributes within the binary to specify code that should be run before registration or unregistration: [ComRegisterFunction] or [ComUnregisterFunction] respectively. The code with the registration and unregistration attributes will be executed even if the process is run under insufficient privileges and fails to execute. You can learn more about this attacker technique at https://attack.mitre.org/wiki/Technique/T1121.
Veramine's detection engine highlights any unknown, new, or suspicious Regsvcs or Regasm image loads. Here we see an example of Regsvcs loading an unsigned DLL that had never previously been loaded by Regsvcs:
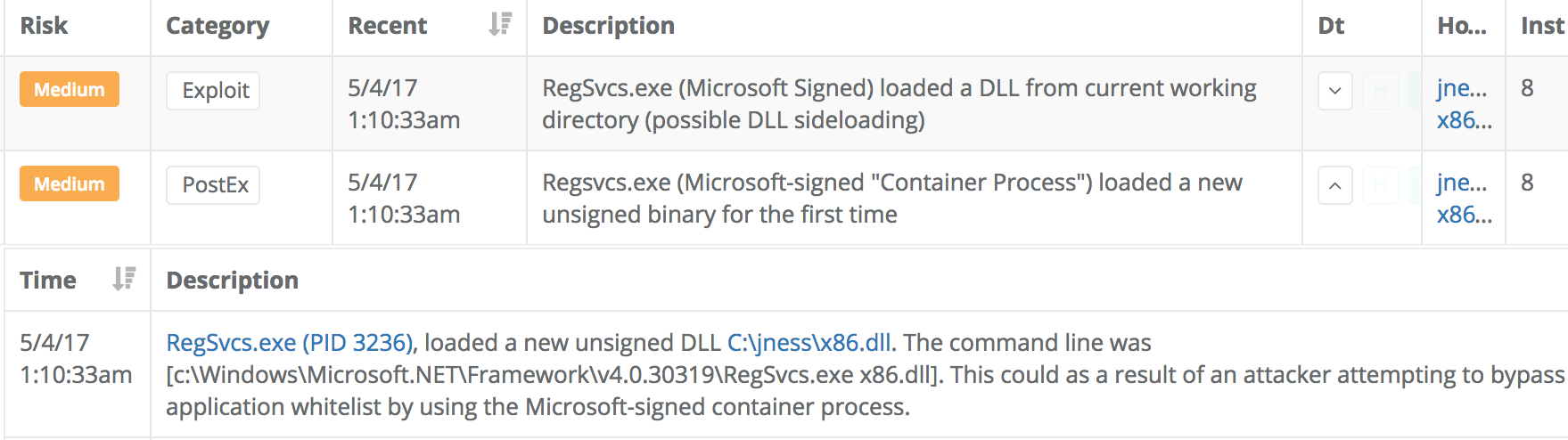
These kind of generic detections can be treated with additional weight when multiple different heuristics indicate suspiciousness. In this case above, we see that the unsigned x86.dll binary had not previously been loaded by Regsvcs but also that it was loaded from the current working directory of the process. Further investigation into the process is just one click away. The process details page shows the full process chain. In this case, regsvcs.exe spawned an additional child process. The new process was a seemingly harmless calc.exe in this case but real-world post-exploitation attacker activity may involve more suspicious-looking processes.
