-
Notifications
You must be signed in to change notification settings - Fork 14
Component Object Model Hijacking
The Microsoft Component Object Model (COM) is a system within Windows to enable interaction between software components through the operating system. Adversaries can use this system to insert malicious code that can be executed in place of legitimate software through hijacking the COM references and relationships as a means for persistence. Hijacking a COM object requires a change in the Windows Registry to replace a reference to a legitimate system component which may cause that component to not work when executed. When that system component is executed through normal system operation the adversary's code will be executed instead. An adversary is likely to hijack objects that are used frequently enough to maintain a consistent level of persistence, but are unlikely to break noticeable functionality within the system as to avoid system instability that could lead to detection. You can read more about this attacker tactic and review several different real-world instances of this tactic at https://attack.mitre.org/wiki/Technique/T1122.
Veramine's detection engine detects certain types of COM hijacking. For example, here is an example of a program adding an Icon Overlay Handler:
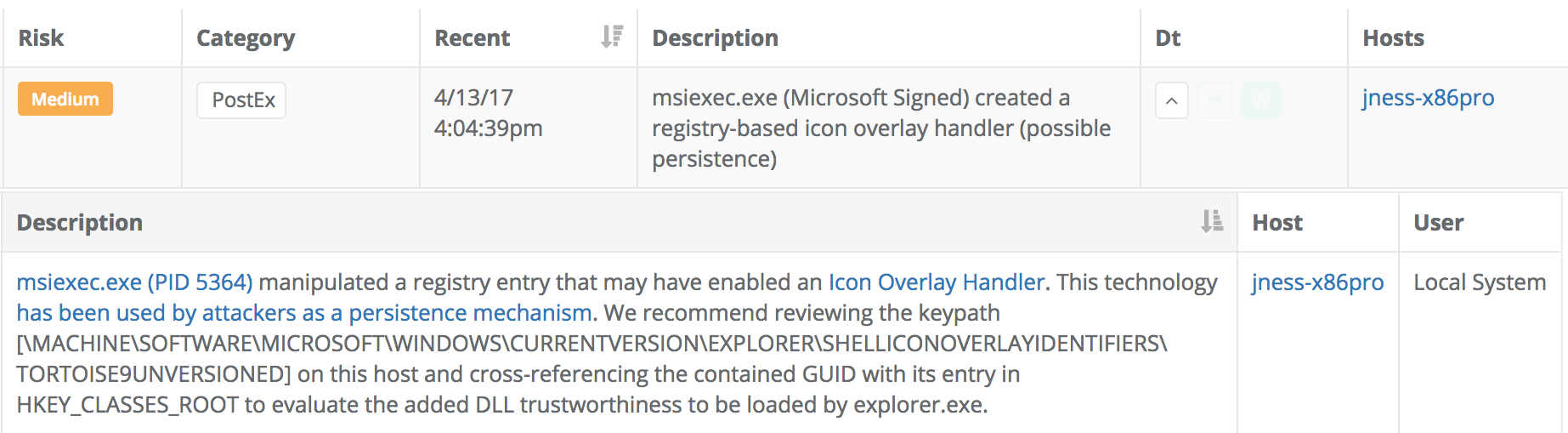
As a defender, you can click on the msiexec.exe (PID 5364) hyperlink to get more context about how the process was launched that created this new icon overlay:
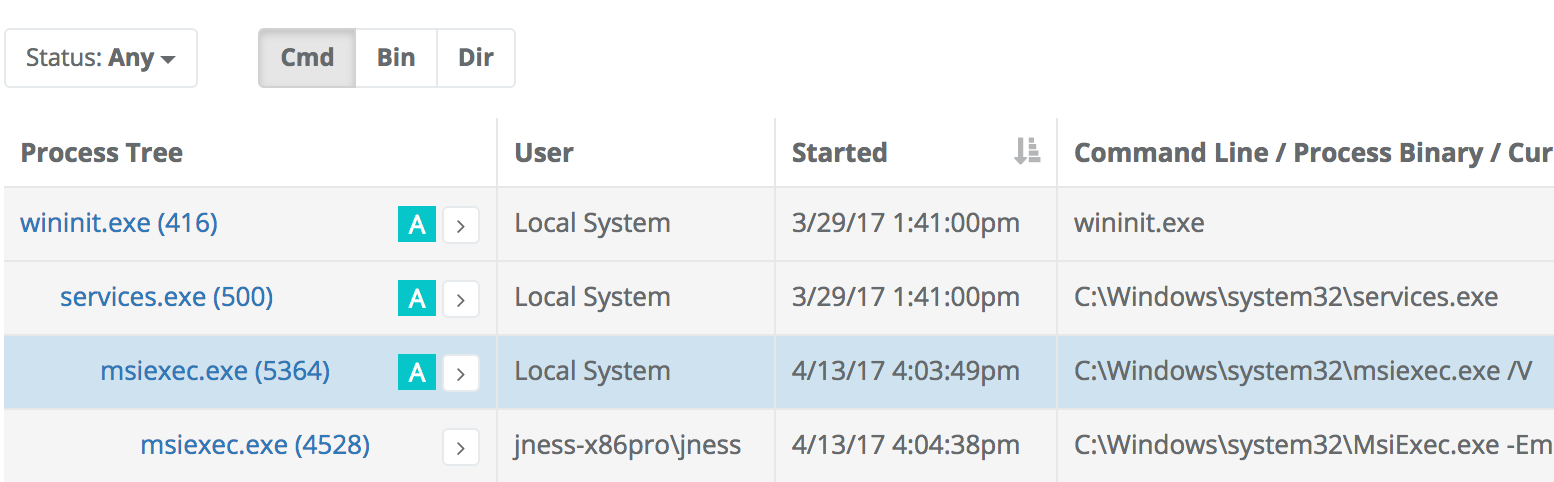
The same process detail page also shows all the binaries loaded by this process. In this case, here were the most recent image loads:
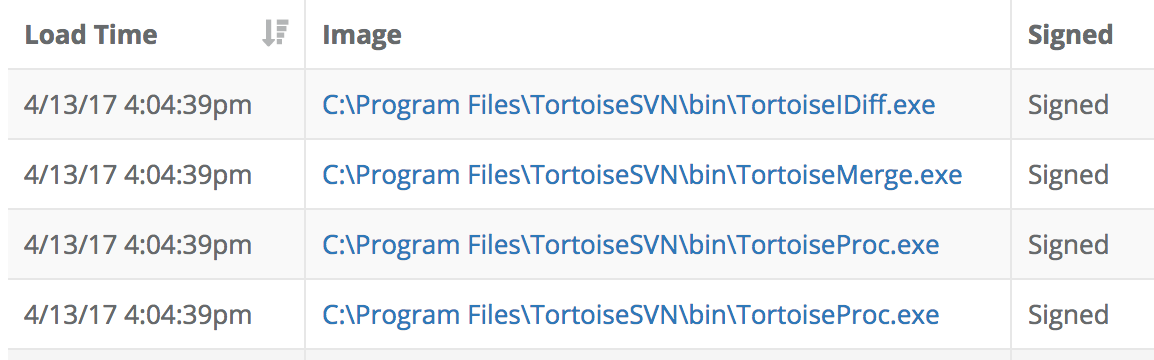
Clicking on any of these binaries reveals this was likely to be a legitimate software install and not an attacker persistence mechanism.

For extra verification, one could click the Download link to get a copy of this binary as the Veramine platform saves a single copy of every binary loaded by any process across the corporate network. If the binary is determined to be malicious or unwanted, the Veramine platform can prevent the binary from being loaded or automatically quarantine any processes loading the binary with a single click of the "Actions" button on that page.