-
Notifications
You must be signed in to change notification settings - Fork 14
DLL Side Loading
Windows programs may specify DLLs that are loaded at runtime. Programs that improperly or vaguely specify a required DLL may be open to a vulnerability in which an unintended DLL is loaded. Side-loading vulnerabilities specifically occur when Windows Side-by-Side (WinSxS) manifests are not explicit enough about characteristics of the DLL to be loaded. Adversaries may take advantage of a legitimate program that is vulnerable to side-loading to load a malicious DLL. More background on these types of attacker tactic available at https://attack.mitre.org/wiki/Technique/T1073 and https://attack.mitre.org/wiki/Technique/T1038.
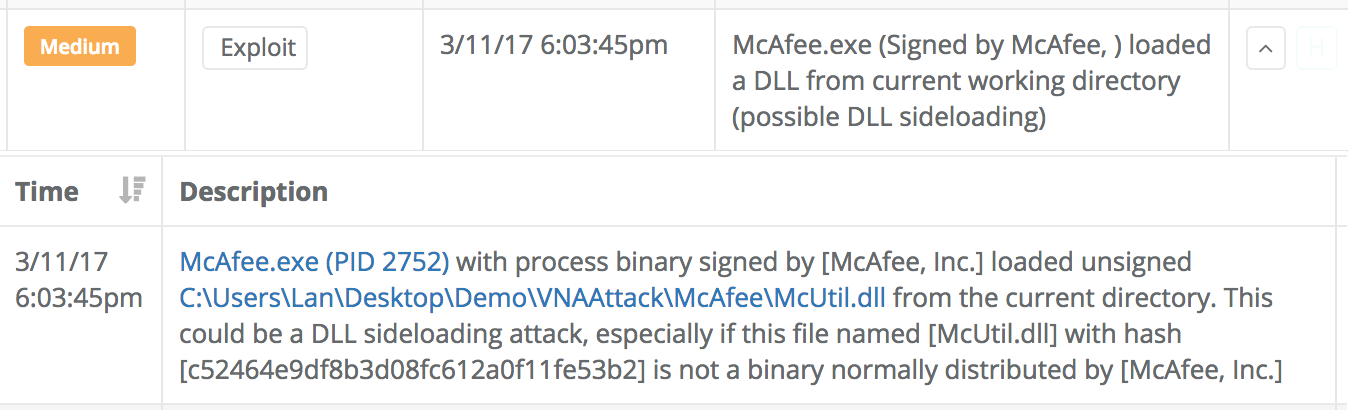
Veramine detects these types of condition by evaluating every image load made by every process. We have a number of heuristics we use to highlight the image loads that match the criteria of a DLL side-loading attack. Here is an example detection of this type of attack: