-
Notifications
You must be signed in to change notification settings - Fork 14
Exploitation of Vulnerability
Exploitation of a software vulnerability occurs when an adversary takes advantage of a programming error in a program, service, or within the operating system software or kernel itself to execute adversary-controlled code. Exploiting software vulnerabilities may allow adversaries to run a command or binary on a remote system for lateral movement, escalate a current process to a higher privilege level, or bypass security mechanisms. Exploits may also allow an adversary access to privileged accounts and credentials. You can read more about this adversary tactic and review an extensive list of examples at https://attack.mitre.org/wiki/Technique/T1068.
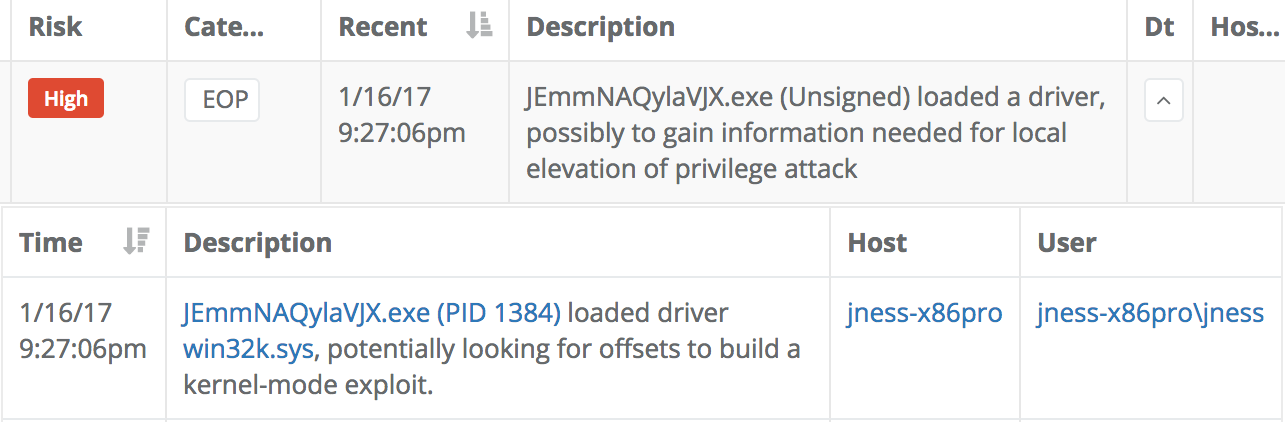
The Veramine detection engine includes robust detection capability of Local Privilege Elevation (LPE) attacks. Many different types of LPE are detected, such as in the following case:
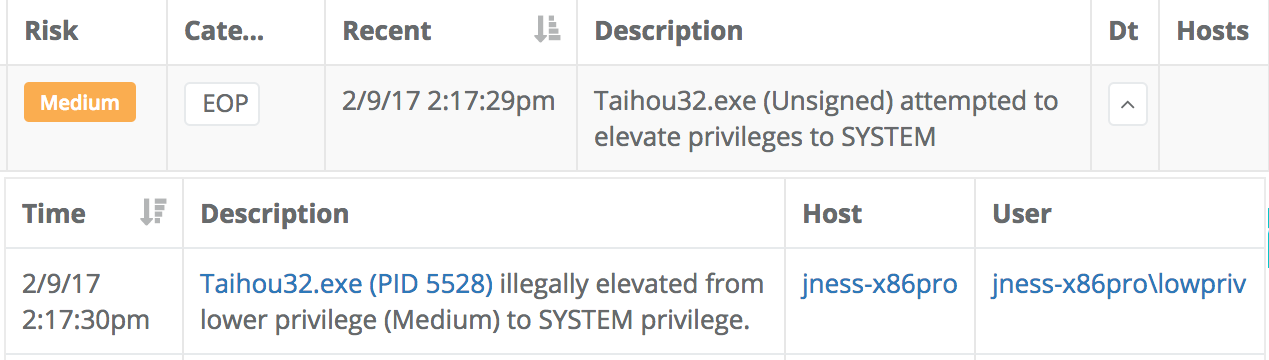
The Veramine detection engine can also often flag the set of behavior that leads up to an attack, even if the subsequent exploit fails due to the vulnerability being patched. Here is one example of the type of leading indicator that often precedes the execution of exploit: