-
Notifications
You must be signed in to change notification settings - Fork 14
File System Permissions Weakness
Processes may automatically execute specific binaries as part of their functionality or to perform other actions. If the permissions on the file system directory containing a target binary, or permissions on the binary itself, are improperly set, then the target binary may be overwritten with another binary using user-level permissions and executed by the original process. If the original process and thread are running under a higher permissions level, then the replaced binary will also execute under higher-level permissions, which could include SYSTEM.
Adversaries may use this technique to replace legitimate binaries with malicious ones as a means of executing code at a higher permissions level. If the executing process is set to run at a specific time or during a certain event (e.g., system bootup) then this technique can also be used for persistence.
The MITRE page at https://attack.mitre.org/wiki/Technique/T1044 highlights two specific file system permissions weaknesses: service binary replacement and instances of executable installers loading from weakly-ACL'd directories. Veramine's detection engine includes several useful detections rules in these scenarios.
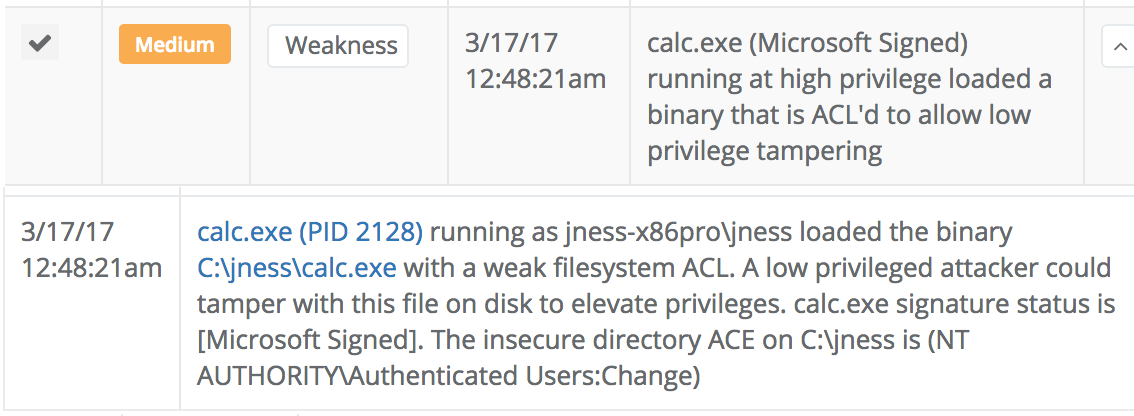
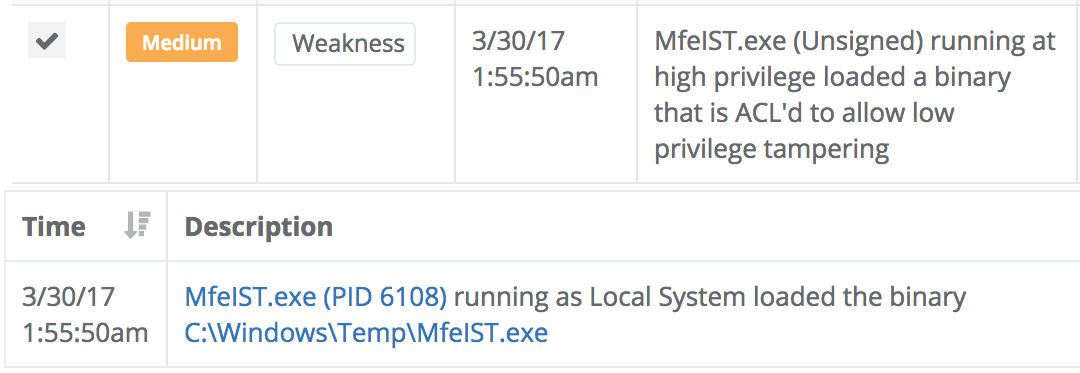
First, the sensor reports every instance where a process running at high privilege loads a binary that is ACL'd to allow low privilege user tampering. Here are a few examples of those detections:
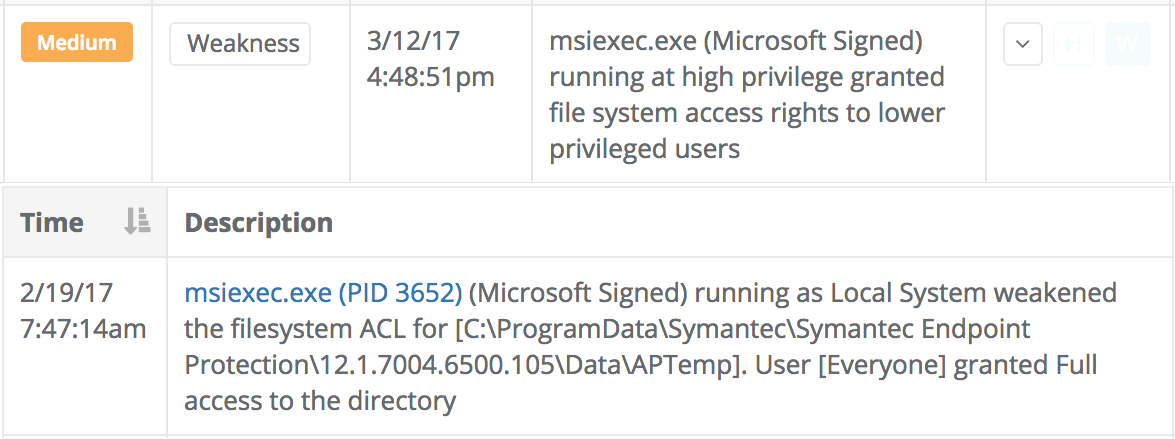
The Veramine detection engine also reports instances where a high privileged process weakens the ACL in such a way that lower privileged users may be able to tamper with the binary in the future. These detections are not necessarily flagging elevation of privilege attacks but rather noting potential newly-created elevation of privilege opportunities that should be evaluated and mitigated. Here is an example:
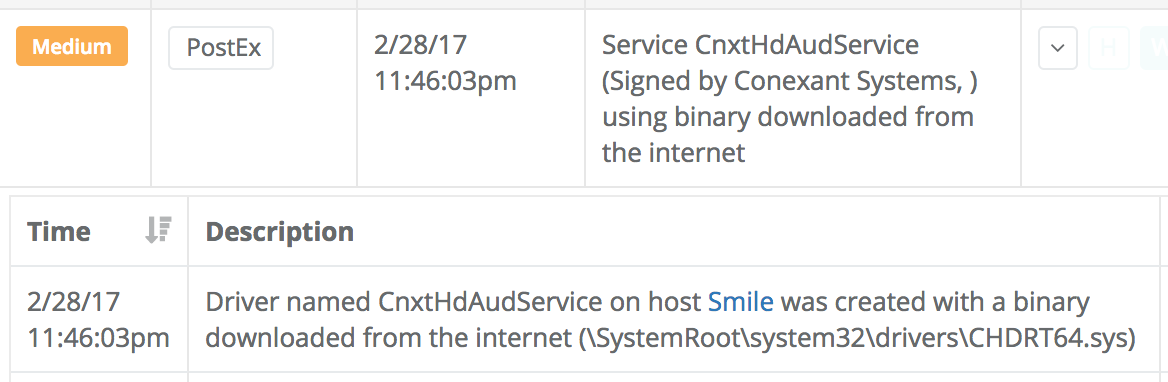
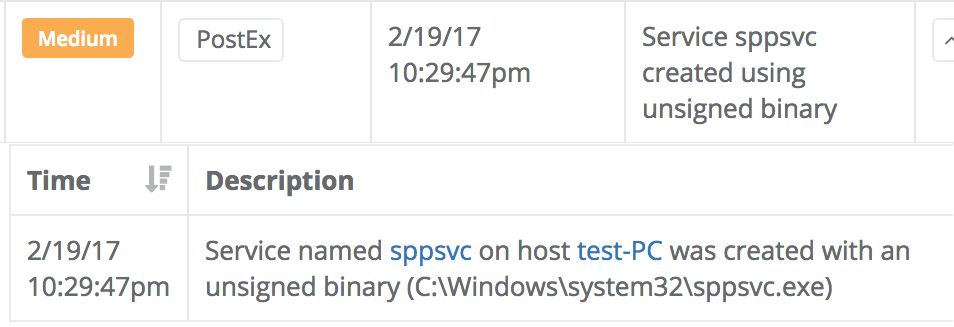
We also detect a few special cases of service binaries that may be interesting based on heuristics we have seen attackers employ. Here are two examples of those suspicious service binary detections: