-
Notifications
You must be signed in to change notification settings - Fork 14
Netsh Helper DLL
Netsh.exe (also referred to as Netshell) is a command-line scripting utility used to interact with the network configuration of a system. It contains functionality to add helper DLLs for extending functionality of the utility. The paths to registered netsh.exe helper DLLs are entered into the Windows Registry at HKLM\SOFTWARE\Microsoft\Netsh.
Adversaries can use netsh.exe with helper DLLs to proxy execution of arbitrary code in a persistent manner when netsh.exe is executed automatically with another Persistence technique or if other persistent software is present on the system that executes netsh.exe as part of its normal functionality. Examples include some VPN software that invoke netsh.exe. You can learn more about this attacker tactic at https://attack.mitre.org/wiki/Technique/T1128.
Veramine's detection engine flags every new added Netsh Helper DLL. Here is an example detection:
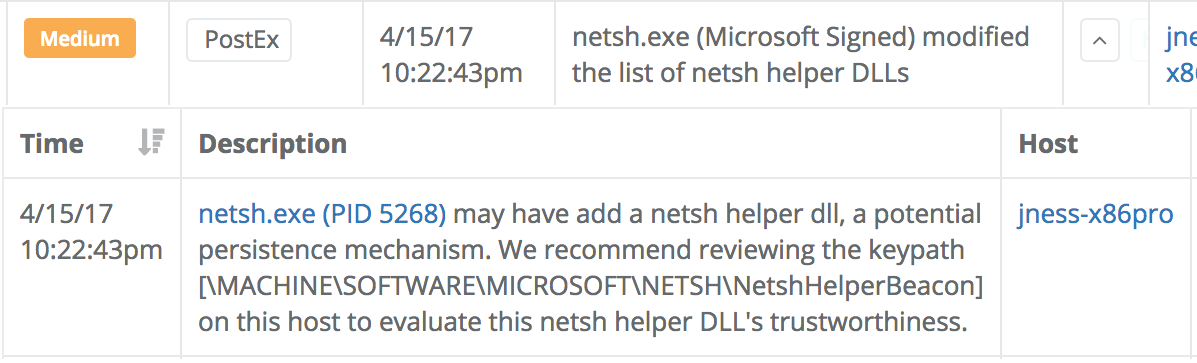
The Veramine rules-based detection algorithm also alerts on all netsh.exe child processes, an additional detection suggestion from the MITRE wiki. That detection looks like this when it is encountered:
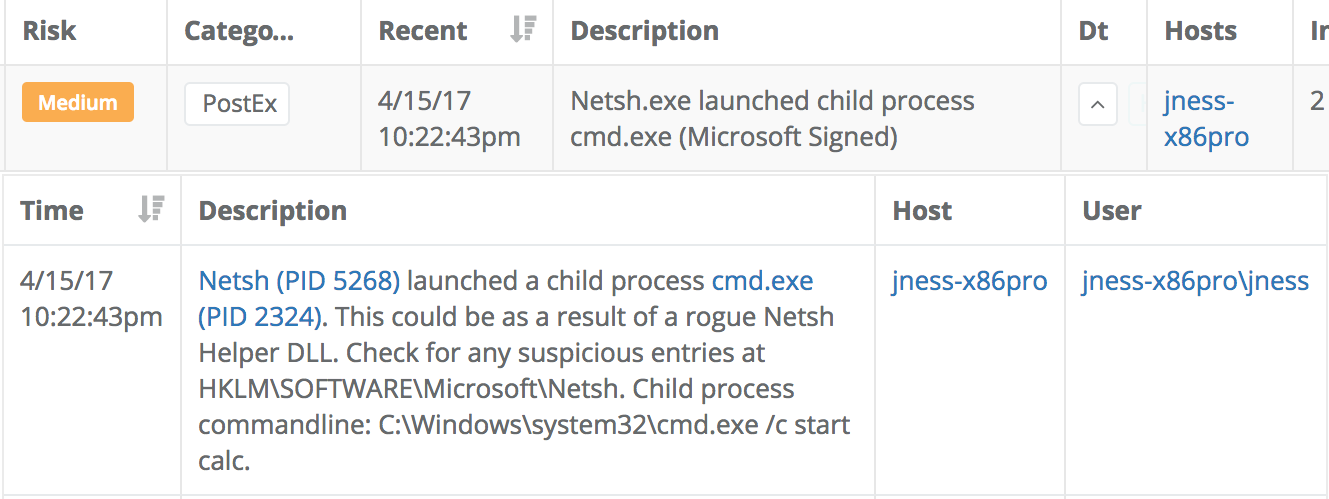
We have seen safe-looking conhost.exe false positive at one of our customers. Here is one example of that:
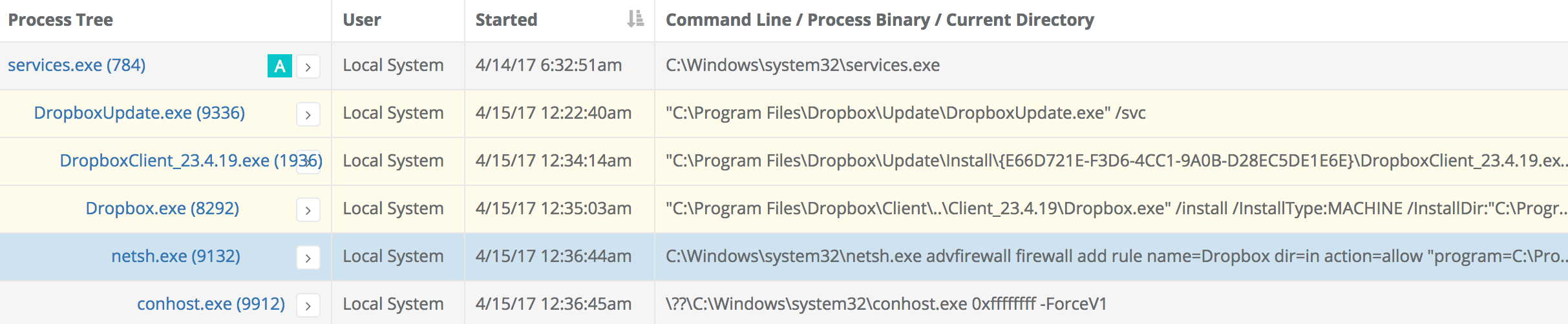
As you can see, this netsh.exe was launched as part of the Dropbox installation to modify the Windows firewall to enable file sharing on the local subnet. For whatever reason as part of that instantiation a conhost.exe also launched and immediately exited. Here are a couple other instances of netsh.exe launching safe-looking child processes:
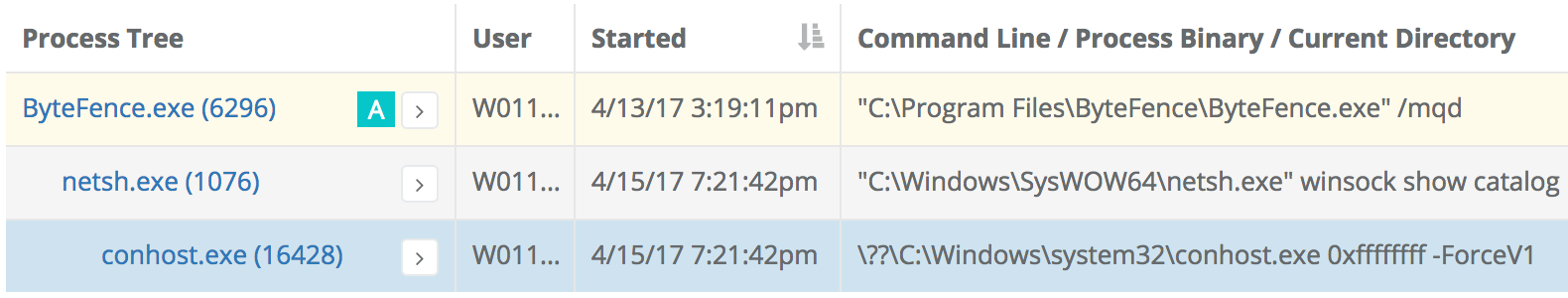

The detection bucket for this rule includes the name of the child process being launched. So if you determine in your environment that conhost.exe is a safe
For more information about Windows Service related tactic detections, please login to the Veramine portal and review the User's Guide Windows Services detection category.