Spring4Shell (CVE-2022-22965) Proof Of Concept/Information + A vulnerable Tomcat server with a vulnerable spring4shell application.
Early this morning, multiple sources has informed of a possible RCE exploit in the popular java framework spring.
The naming of this flaw is based on the similarities to the infamous Log4j LOG4Shell.
- https://websecured.io/blog/624411cf775ad17d72274d16/spring4shell-poc
- https://www.springcloud.io/post/2022-03/spring-0day-vulnerability
- https://spring.io/blog/2022/03/31/spring-framework-rce-early-announcement
The usage is simple! You can either run the docker image, or just run the python script!
Please see vulnerable-tomcat for inscructions on setting up your own spring4shell vulnerable application here!
- Python3 or Docker
pip install -r requirements.txt
poc.py --help## Dockerhub
docker pull bobtheshoplifter/spring4shell-poc:latest
docker run bobtheshoplifter/spring4shell-poc:latest --url https://example.io/
## Github docker repository
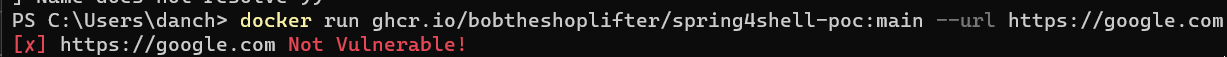
docker pull ghcr.io/bobtheshoplifter/spring4shell-poc:main
docker run ghcr.io/bobtheshoplifter/spring4shell-poc:main --url https://example.io/I have now made a docker image for this, which includes a vulnerable spring + tomcat application.
The application should be enough to test this vulnerability.
Please see (vulnerable-tomcat/README.md)
!!(The following mitigations are only theoretical as nothing has been confirmed)!!
Cyberkendra informed that JDK versions lower than JDK 9
You can easily check this by running
java -versionThat will display something similar to this
openjdk version "17.0.2" 2022-01-18
OpenJDK Runtime Environment (build 17.0.2+8-Ubuntu-120.04)
OpenJDK 64-Bit Server VM (build 17.0.2+8-Ubuntu-120.04, mixed mode, sharing)If your JDK version is under 8, you might be safe, but nothing is confirmed yet
The following article will be updated
Do a global search after spring-beans*.jar and spring*.jar
find . -name spring-beans*.jarPOC, translated fron this repository: https://github.com/craig/SpringCore0day/blob/main/exp.py