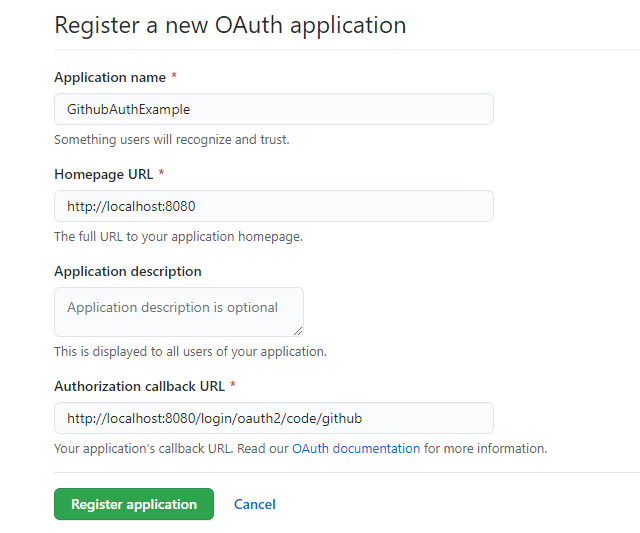
Create github auth application : Visit https://github.com/settings/applications/new and follow screenshot.
To enable Spring Security OAuth 2.0, we need to add the following starter: org.springframework.boot spring-boot-starter-oauth2-client
Now, we’ll need to modify our application.yml:
spring:
security:
oauth2:
client:
registration:
github:
clientId: ${GITHUB_CLIENT_ID} Here you can add your keys
clientSecret: ${GITHUB_CLIENT_SECRET} Here you can add your keys
The GITHUB_CLIENT_ID and the GITHUB_CLIENT_SECRET are environment variables that hold the values that you get back once you register your application on GitHub (same for Google, Facebook, or any other provider).
Now let’s configure our security:
@EnableWebSecurity
public class SecurityConfig extends WebSecurityConfigurerAdapter {
@Override
protected void configure(HttpSecurity http) throws Exception {
http.authorizeRequests()
.anyRequest().authenticated()
.and()
.oauth2Login();
}
}
In the above code, we want every request to be authenticated. We add oauth2Login in order to configure authentication support using OAuth 2.0.
Now if we try to access localhost:8080 in our browser, we’ll be forwarded to the GitHub sign-in page:

So what happened here? When a request is made to localhost:8080, Spring security will try to find an authenticated object, but eventually, it fails to. So it redirects to: http://localhost:8080/oauth2/authorization/github
Internally, this request is getting handled by OAuth2AuthorizationRequestRedirectFilter, which uses implements doFilterInternal that matches against the /oauth2/authorization/github URI and redirect the request to
https://github.com/login/oauth/authorize?response_type=code&client_id=&scope=read:user&state=&redirect_uri=http://localhost:8080/login/oauth2/code/github the above redirect_uri contains the same value we put when we registered our application.
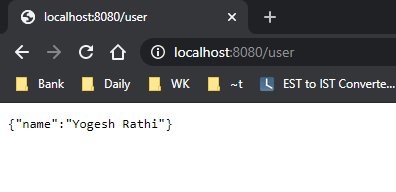
#You can call http://localhost:8080/user api and see magic
It’s very simple to build an application with “social login” using OAuth 2.0 and Spring Boot.