-
Notifications
You must be signed in to change notification settings - Fork 17
use case 3
Related artifacts:
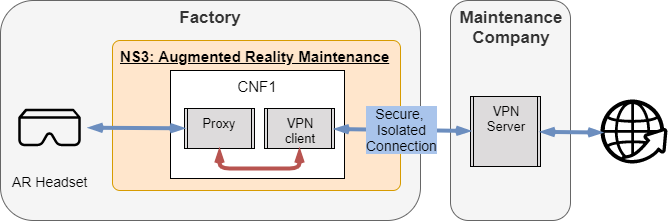
- Hololens used for remote maintenance at Weidmüller
- Connects via an access point to Weidmüller Kubernetes server
- On the server, a proxy and VPN client is running as a CNF/Docker container on k8s
- The VPN client connects to the VPN server, which is running on a VM at UPB
- The Hololense connects via the proxy and the VPN connection to the internet such that the traffic is isolated and secure
Problem: Skype traffic uses many TCP and UPD ports and not just HTTP and sends traffic not through the proxy... But sufficient for Skype control traffic and any other video streams, eg, YT, or websites.
- Using
fgcn-tango-vpn.cs.upb.deas VPN server and CA machine - OpenVPN default port is 1194, which is open from the outside (not just within University network)
The server setup is explained here.
Option 1 (recommended): Pull the image from Docker hub
docker pull sonatanfv/vnf-proxyvpn:latest
Option 2: Build the image manually using the Dockerfile
cd vnfs
./build_usecase3_proxyvpn.sh
Start the proxy and VPN client in a container. Needs privileged mode to enable tunneling (does not work on Windows!).
docker run -d --rm -p 3128:3128 -p 1194:1194/udp --privileged --name vnf-proxyvpn sonatanfv/vnf-proxyvpn:latest
# alternative to --privileged for docker 1.2+
docker run -d --rm -p 3128:3128 -p 1194:1194/udp --cap-add=NET_ADMIN --device /dev/net/tun --name vnf-proxyvpn sonatanfv/vnf-proxyvpn:latest
First check the local IP address without the proxy and VPN connection:
curl ifconfig.me
This should return your local IP address. Then do a curl using the container as proxy (port 3128):
curl --proxy 127.0.0.1:3128 ifconfig.me
This should show the IP address of the VPN server, which is 131.234.28.141, not your local IP address.
Strangely, this doesn't work when running the container on another machine and trying to access it remotely.
With Firefox, configure the proxy settings via the browser's preferences (network settings). Chrome uses the system-wide configured proxy (Ubuntu GUI: Settings, Netework Proxy).
Proxy settings: Manual. Proxy 127.0.0.1 for HTTP, HTTPS, etc. with port 3128.
If no GUI is available via the command line:
export HTTPS_PROXY=172.17.0.1:3128 # or HTTP_PROXY
Then Internet access should only be possible if the container is running. Try to access any website or streaming a video.
A nice video for a demo is this Weidmüller training video: https://www.youtube.com/watch?v=lCZodLZuwvs
Since there may be issues accessing the VPN+proxy container remotely, a simple alternative for a live demo is just using a proxy without VPN. It still allows providing connectivity on demand and filtering/limiting traffic to certain destinations.
docker pull sonatanfv/vnf-proxy:latest
# or build manually
cd vnfs
./build_usecase3_proxy.sh
docker run -d --rm -p 3128:3128 --name vnf-proxy sonatanfv/vnf-proxy:latest
Do a simple curl using the container as proxy (port 3128) and see if the connection works:
curl --proxy 127.0.0.1:3128 google.com
This should return some HTML ("...The document has moved..."). If there's a timeout or connection refused, the proxy isn't working.
Similarly, this should work from another machine in the same network:
curl --proxy <ip-of-proxy-machine> google.com
After stopping the proxy container, the command should time out.
With Firefox, configure the proxy settings via the browser's preferences (network settings). Chrome uses the system-wide configured proxy (Ubuntu GUI: Settings, Netework Proxy).
Proxy settings: Manual. Proxy 127.0.0.1 for HTTP, HTTPS, etc. with port 3128.
If no GUI is available via the command line:
export HTTPS_PROXY=172.17.0.1:3128 # or HTTP_PROXY
Then Internet access should only be possible if the container is running. Try to access any website or streaming a video.
Activate the venv in which tng-cli is installed (or install it).
Set the URL or the Tango SP:
export SP_PATH=http://int-sp-ath.5gtango.eu
Package:
cd sdk-projects
./pack-ns3-k8s.sh
On-board:
tng-cli package -u eu.5gtango.tng-smpilot-ns3-k8s.0.1.tgo
- Go to https://int-sp-ath.5gtango.eu/service-management/network-services/services
- Click the instantiate (play) button next to NS3. Keep default values and choose some name, eg,
sm-ns3 - After confirming instantiation, the request should be visible under "Requests" and after about 30s the running instance should be listed under "Network Services > Instances"
- Go to https://int-sp-ath.5gtango.eu/service-management/network-services/network-service-instances
- Select the running NS3 instance
- On the page with details about the instance, scroll down to "CNF instances" and select the "smpilot-connector" CNF
- Copy the "Floating IP"
Test if you can connect using the floating IP, eg, using curl:
curl --proxy <floating-ip>:3128 google.com
In the end, terminate the service instance by clicking the terminate (stop) button in the Tango SP portal.
- Create tunnel interfaces at computer/access point of Hololens and at container
- Tunnel all traffic, including Skype traffic
- Need root permissions in container for creating tunnel interfaces
- http://www.dest-unreach.org/socat/doc/socat-tun.html
- Simple, but probably slow
Or build it manually:
cd vnfs
./build_usecase3.sh
Run container with Socat TUN server:
docker run -d --rm -p 11443:11443 --privileged --name vnf-socat sonatanfv/vnf-socat:latest
Connect to running container with Socat TUN client (on same machine). This will block. can be terminated with ctrl+c, which will also stop the docker container.
sudo socat TCP:127.0.0.1:11443 TUN:192.168.255.2/24,up
# alternatively from another machine, replace 127.0.0.1 with the IP/DNS of the first machine, eg:
sudo socat TCP:schneider-dev.cs.upb.de:11443 TUN:192.168.255.2/24,up
Test the connection (on same machine, new terminal):
# on the machine, ping the Docker container
ping 192.168.255.1
https://how-to.fandom.com/wiki/How_to_set_up_a_NAT_router_on_a_Linux-based_computer
https://www.revsys.com/writings/quicktips/nat.html
Use the server's tunnel interface (IP 192.168.255.1) as default gateway for all Internet traffic:
# check existing routes
route -n
# add new default gw
sudo route add default gw 192.168.255.1
# check again that the new route is there
route -n
Ensure that IP forwarding is enabled:
sysctl net.ipv4.ip_forward # should be 1, not 0
# else
echo 1 > /proc/sys/net/ipv4/ip_forward
Share the Internet access from eth0 through the tunnel interface tun0 (NAT):
iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
iptables -A FORWARD -i eth0 -o tun0 -m state --state RELATED,ESTABLISHED -j ACCEPT
iptables -A FORWARD -i tun0 -o eth0 -j ACCEPT
In theory this should now allow pinging any public IP address (eg 216.58.207.46 of Google) from the client via the tunnel through the server's internet access. Unfortunately, it doesn't work (for me).
- I don't have Internet access anymore on the client. Pinging doesn't work.
- During
ping, the TX packet counter at the client increases, so the client configuration seems to work and send all traffic to the tunnel interface - But the RX packet count at the server does not increase. So the packets apparently don't even arrive at the server. Neither for public IPs nor for the IP of the server's tunnel interface.
- Is it possible that the
sudo route add default gw 192.168.255.1destroys the Internet connection over which the tunnel works such that the tunnel doesn't work anymore?
- Try pinging each other and outside IP addresses.
- Use
watch ifconfigto see if the packet counter is increasing and for which interface. - The
tun0interface only shows up inifconfigaftersocatis started on both client and server.