This project is to reverse engineer the Kmove / DIERYA DK63 to get QMK running on it. Use this information at your own risk. I'm not liable if you break something.
- Identify MCU
VS11K09A-1/Sonix SN32F248BF - Find data sheet VS11K09A-1 / Sonix SN32F248B
- Find SDK and dev tools
- Get SWD working
- Ability to flash firmware
- Get origional firmware
- Enable SWD in current firmware
- Port Chibios to
Sonix SN32F248BFporting guide-
Get compiler to work withSN32F248BFKeil packs - USB LLD
- GPIO LLD
-
UART LLD - Timers LLD
- SPI LLD
-
I2C LLD
-
- Get QMK firmware working
- Basic keyboard functionality Build Tools
- RGB Leds and animations
VSPW01RGB Matrix - Bluetooth
PAR2801QN-GHVCdocs
- Dump origional bootloader
- Main MCU - EVision VS11K09A-1, Seems to be based on the Sonix SN32F248BF
- Bluetooth -
!TONPXI Pixart PAR2801QN-GHVC LED driverCharging Chip - EVision VSPW01
- Hookup SWCLK, SWDIO, and Ground using the testpoints outlined below
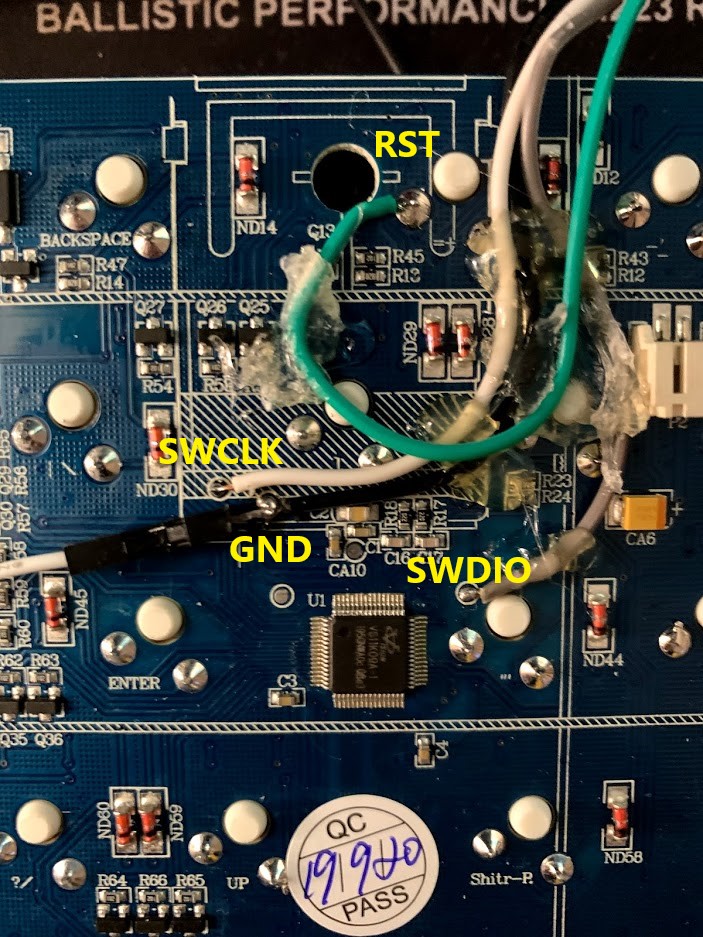
- Note: These pins are being use by the MCU to control functionality. Im tyring to enable SWD in the default firmware to debug without Debug Recovery Mode.
- Hookup the other ends of the wires to your debugger. I used a Raspberry PI 3 and the ST-Link V2.
- Using the ground point hold the boot pin to ground while turning on the power.
They seem to be driven by GPIO and transistors.
- Figure out pin map and matrix
- Caps lock LED
Appears to be an another ARM Cortex M0 MCU with UART and GPIO.
- SWD debugging
- Pin map to main MCU
- Download Resource Hacker (Not sure of a mac or linux variant)
- Download Firmware Update tool
- Extract the firmware .rar and open the .exe in RH
- Look for
RCData 4000:0, this is the hex file of the firmware - Right click on
4000:0and chooseSave Resource to BIN file - Save the firmware so it can be examined or uplodaded.
- Download the USB MCU ISP tool
- Open the program and click load file.
- Select
SN32F4xBand then the firmware file. - The VID should alread be
0C45and enter766Bfor the PID. - Click Start
- Profit!
- I was not able to get this to work with the st-link software on windows.
- I did manage to get it to work with openocd using this config
- Working on the
SN32F24Xconfig here
- set $pc=0x1FFF0301
- cont
- Ghidra
- SVD-Loader for Ghidra automates the entire generation of peripheral structs and memory maps for over 650 different microcontrollers
- Binary Ninja
- Cutter
- radare2
- Wireshark USB caprture
- Firmware patch framework nexmon
- ARM Assembly Tutorial
Firmware Updater Executable Analysis https://www.hybrid-analysis.com/sample/21cf79c4f5982e0d73e8269c03a043f16898292920074491d5452eea5155e1eb?environmentId=100
VS11K09A-1 VS 32-Bit Cortex-M0 Micro-Controller http://evision.net.cn/include/upload/kind/file/20190413/20190413174647_5965.pdf
DEF CON 26 IoT VILLAGE - Dennis Giese - How to modify ARM Cortex M based firmware A step by step app https://www.youtube.com/watch?v=Qvxa6o2oNS0
BalCCon2k16 - Travis Goodspeed - Nifty Tricks for ARM Firmware Reverse Engineering https://www.youtube.com/watch?v=GX8-K4TssjY
Getting STLink V2 Serial Number https://armprojects.wordpress.com/2016/08/21/debugging-multiple-stm32-in-eclipse-with-st-link-v2-and-openocd/
SUE 2017 - Reverse Engineering Embedded ARM Devices - by pancake https://www.youtube.com/watch?v=oXSx0Qo2Upk
Analyzing Keyboard Firmware https://mrexodia.github.io/reversing/2019/09/28/Analyzing-keyboard-firmware-part-1 https://mrexodia.github.io/reversing/2019/09/28/Analyzing-keyboard-firmware-part-2 https://mrexodia.github.io/reversing/2019/09/28/Analyzing-keyboard-firmware-part-3
Hacking the fx-CP400 https://the6p4c.github.io/2018/01/15/hacking-the-gc-part-1.html
Raspberry PI OpenOCD SWD / JTAG https://iosoft.blog/2019/01/28/raspberry-pi-openocd/
OpenOcd Creating Flash Drivers https://github.com/doctek/COOCDFlash/wiki/Creating-and-using-flash-drivers
Stack Exchange ARM Firmware Reverse Engineering Walkthrough https://reverseengineering.stackexchange.com/questions/15311/running-a-binary-identified-as-an-arm-excutable-by-binwalk-disasm/15317 https://reverseengineering.stackexchange.com/questions/15006/approach-to-extract-useful-information-from-binary-file
QMK Nuvoton Port PR [qmk/ChibiOS-Contrib#10]
- https://docs.qmk.fm/
- https://github.com/qmk/qmk_firmware/blob/ee700b2e831067bdb7584425569b61bc6329247b/tmk_core/protocol/chibios/README.md
- http://wiki.chibios.org/dokuwiki/doku.php?id=chibios:guides:port_guide
- https://github.com/ChibiOS/ChibiOS/tree/14f274991fc85b70dd4294c482f6d4ce79e72339/os/hal/boards/OLIMEX_MSP430_P1611
- http://www.sonix.com.tw/article-en-998-21393
- https://ydiaeresis.wordpress.com/2018/04/23/i-dont-steal-bikes-part-2/
- https://interrupt.memfault.com/blog/cortex-m-fault-debug#registers-prior-to-exception
- https://github.com/bnahill/PyCortexMDebug
- http://zuendmasse.de/blog/2018/01/21/gdb-+-svd/