-
Notifications
You must be signed in to change notification settings - Fork 43
Commit
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
- Loading branch information
1 parent
4c4f50e
commit c867816
Showing
1 changed file
with
33 additions
and
76 deletions.
There are no files selected for viewing
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -1,103 +1,60 @@ | ||
|
|
||
| <h1 align="center"> | ||
| <br> | ||
| <a href="https://github.com/ankitdobhal/Ashok"><img src="https://dev-to-uploads.s3.amazonaws.com/i/vbm48fw5v25qju2h8lr4.png" alt="Ashok"></a> | ||
| <a href="https://github.com/ankitdobhal/Ashok"><img src="https://dev-to-uploads.s3.amazonaws.com/i/zme8dd2tch116ykohbkb.png" alt="Ashok"></a> | ||
| <br> | ||
| Ashok | ||
| <br> | ||
| </h1> | ||
|
|
||
| <h4 align="center">Osint Recon Swiss Army Knife</h4> | ||
|
|
||
| ## Main Features | ||
| ```python | ||
| [+] 1 - HTTP Header Checker | ||
|
|
||
| [+] 2 - Whois Lookup | ||
|
|
||
| [+] 3 - Dns Lookup | ||
|
|
||
| [+] 4 - Banner Graber | ||
|
|
||
| [+] 5 - Github Information Extractor | ||
| <h4 align="center">Incredible Fast Recon Swiss Army Knife</h4> | ||
| <p align="center"> | ||
| <a href="https://github.com/ankitdobhal/Ashok/releases"> | ||
| <img src="https://img.shields.io/github/release/ankitdobhal/Ashok.svg"> | ||
| </a> | ||
| </p> | ||
|
|
||
| [+] 6 - Nmap Scan | ||
| ## Introduction | ||
| Reconnaissance is the first phase of penetration testing which means gathering information before any real attacks are planned So Ashok is an Incredible fast recon tool for penetration tester which is specially designed for Reconnaissance phase. And in [Ashok-v1.1](https://github.com/ankitdobhal/Ashok/releases) you can find the **[advanced google dorker]() and [wayback crawling machine]().** | ||
|
|
||
| [+] 7 - Link Extractor | ||
|  | ||
|
|
||
| [+] 8 - Subdomain Identifier | ||
|
|
||
| [+] 9 - Subnet Lookup | ||
|
|
||
| [+] 10 - Cms/Technology Detector With Custom Headers | ||
|
|
||
| [+] 11 - Geoip Lookup | ||
| ## Main Features | ||
| ```python | ||
| - Wayback Crawler Machine | ||
| - Google Dorking without limits | ||
| - Github Information Grabbing | ||
| - Subdomain Identifier | ||
| - Cms/Technology Detector With Custom Headers | ||
| ``` | ||
|
|
||
| ## Compatibility | ||
| Ashok is a Osint Recon Swiss Army Knife, It is still in a beta state so it it not compatible with windows .It will run with following configuration: | ||
| * Operating Systems: Linux, Mac | ||
| * Python Versions: Python3.5, Python 3.7 | ||
|
|
||
| ## Installation | ||
| Ashok is very simple to install with the following steps : | ||
|
|
||
| ``` | ||
| ~> git clone https://github.com/ankitdobhal/Ashok | ||
| ~> cd Ashok | ||
| ~> pip3 install -r requirements.txt | ||
| ~> python3 Ashok.py -h | ||
| ``` | ||
|
|
||
| ## Usage | ||
|
|
||
| Ashok is a beginners friendly tool for beginners in penetration testing and OSINT, it can be used with the following command and examples. | ||
|
|
||
| **[+] Note : You can check whole help page of Ashok with the following command :** | ||
|
|
||
| ```bash | ||
| ~> python3 Ashok.py -h | ||
| ~> python3.7 -m pip3 install -r requirements.txt | ||
| ``` | ||
| 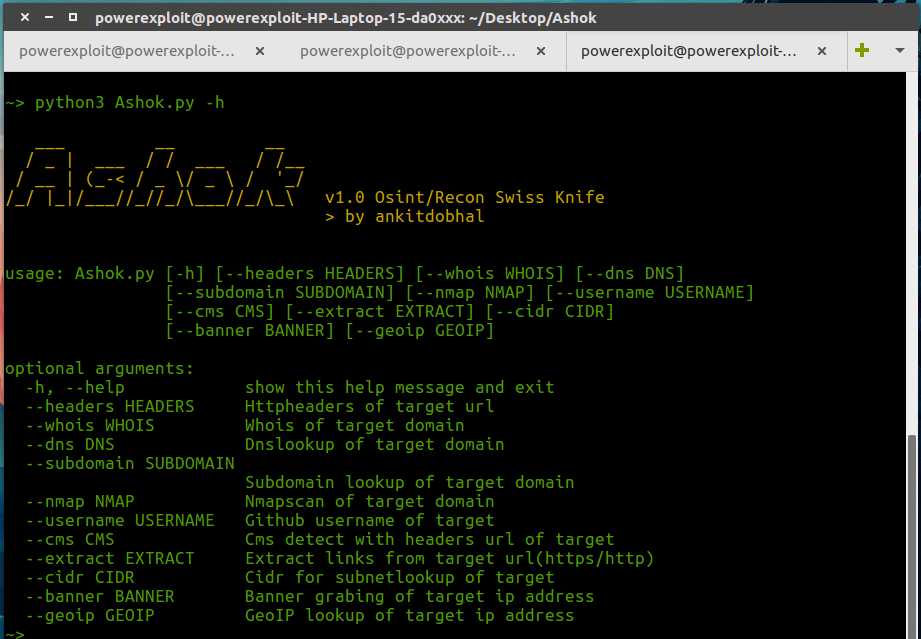 | ||
|
|
||
| **Here are some basic example to use Ashok for your Osint recon :** | ||
| ## How to use Ashok? | ||
| A detailed usage guide is available on [Usage](https://github.com/ankitdobhal/Ashok/wiki/Usage) section of the [Wiki](https://github.com/ankitdobhal/Ashok.git). | ||
|
|
||
| **1. HTTP Header Checker** | ||
| ``` | ||
| ~> python3 Ashok.py --headers domain_name | ||
| example : python3 Ashok.py --headers example.com | ||
| ``` | ||
| But Some index of options is given below: | ||
|
|
||
| **2. Whois Lookup** | ||
| ```bash | ||
| ~> python3 Ashok.py --whois domain_name | ||
| example : python3 Ashok.py --whois example.com | ||
| ``` | ||
|
|
||
| **3.Banner Graber** | ||
| ```bash | ||
| ~> python3 Ashok.py --banner ip_address | ||
| example : python3 Ashok.py --banner 8.8.8.8 | ||
| ``` | ||
|
|
||
| **4. Github Information Extractor** | ||
| ```bash | ||
| ~> python3 Ashok.py --username username_of_github_user | ||
| example : python3 Ashok.py --username Elliot | ||
| ``` | ||
|
|
||
| **5. Cms/Technology Detector With Custom Headers** | ||
| ```bash | ||
| ~> python3 Ashok.py --cms url_of_target | ||
| example : python3 Ashok.py --cms https://www.example.com | ||
| ``` | ||
| - [Extract Http Headers from single url](https://github.com/ankitdobhal/Ashok/wiki/Usage#Extract-Http-Headers-from-single-url) | ||
| - [Dump internet-archive machine with json output for single url](https://github.com/ankitdobhal/Ashok/wiki/Usage#Dump-internet-archive-machive-with-json-output-for-single-url) | ||
| - [Google dorking using number of results as dorknumber](https://github.com/ankitdobhal/Ashok/wiki/Usage#Google-dorking-using-number-of-results-as-dorknumber) | ||
| - [Dns Lookup of single target domain](https://github.com/ankitdobhal/Ashok/wiki/Usage#Dns-Lookup-of-single-target-domain) | ||
| - [Subdomain Lookup of single target domain](https://github.com/ankitdobhl/Ashok/wiki/Usage#Subdomain-Lookup-of-single-target-domain) | ||
| - [Port Scan using nmap of single target domain](https://github.com/ankitdobhal/Ashok/wiki/Usage#Port-Scan-using-nmap-of-single-target-domain) | ||
| - [Extract data using Github username of target](https://github.com/ankitdobhal/Ashok/wiki/Usage#Extract-data-using-Github-username-of-target) | ||
| - [Detect Cms of target url](https://github.com/ankitdobhal/Ashok/wiki/Usage#Detect-Cms-of-target-url) | ||
|
|
||
| ## Contribution & License | ||
| ## Contribution | ||
| You can contribute in following ways: | ||
|
|
||
| - Report bugs | ||
| - Develop plugins | ||
| - Develop tool | ||
| - Give suggestions to make it better | ||
| - Fix issues & submit a pull request | ||
|
|
||
| ## Credits | ||
| * [hackertarget](https://hackertarget.com/) | ||
| * [hackertarget](https://hackertarget.com/) |