v1.3.0
We are thrilled to announce the release of Ory Kratos v1.3.0! This release includes significant updates, enhancements, and fixes to improve your experience with Ory Kratos.
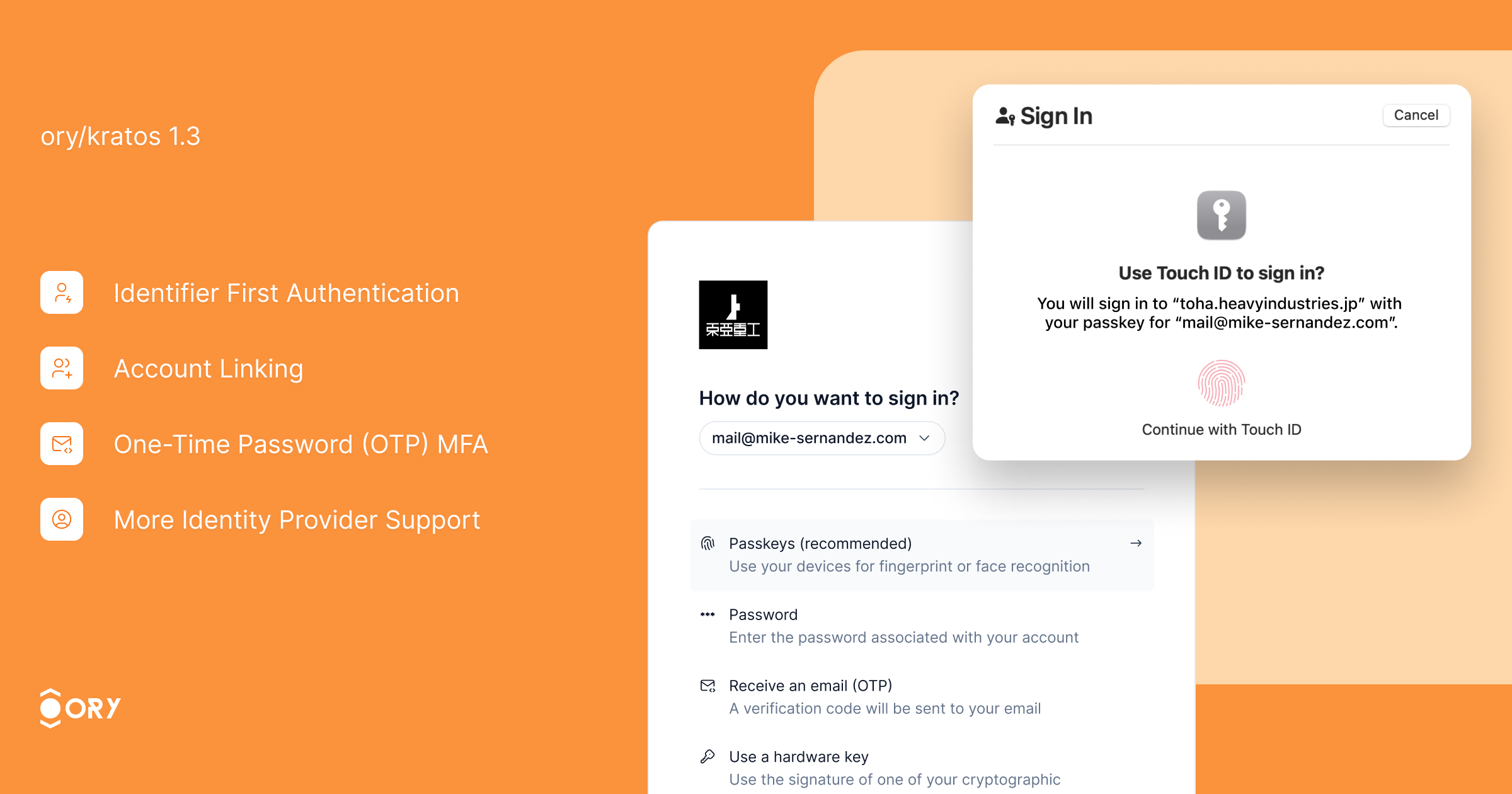
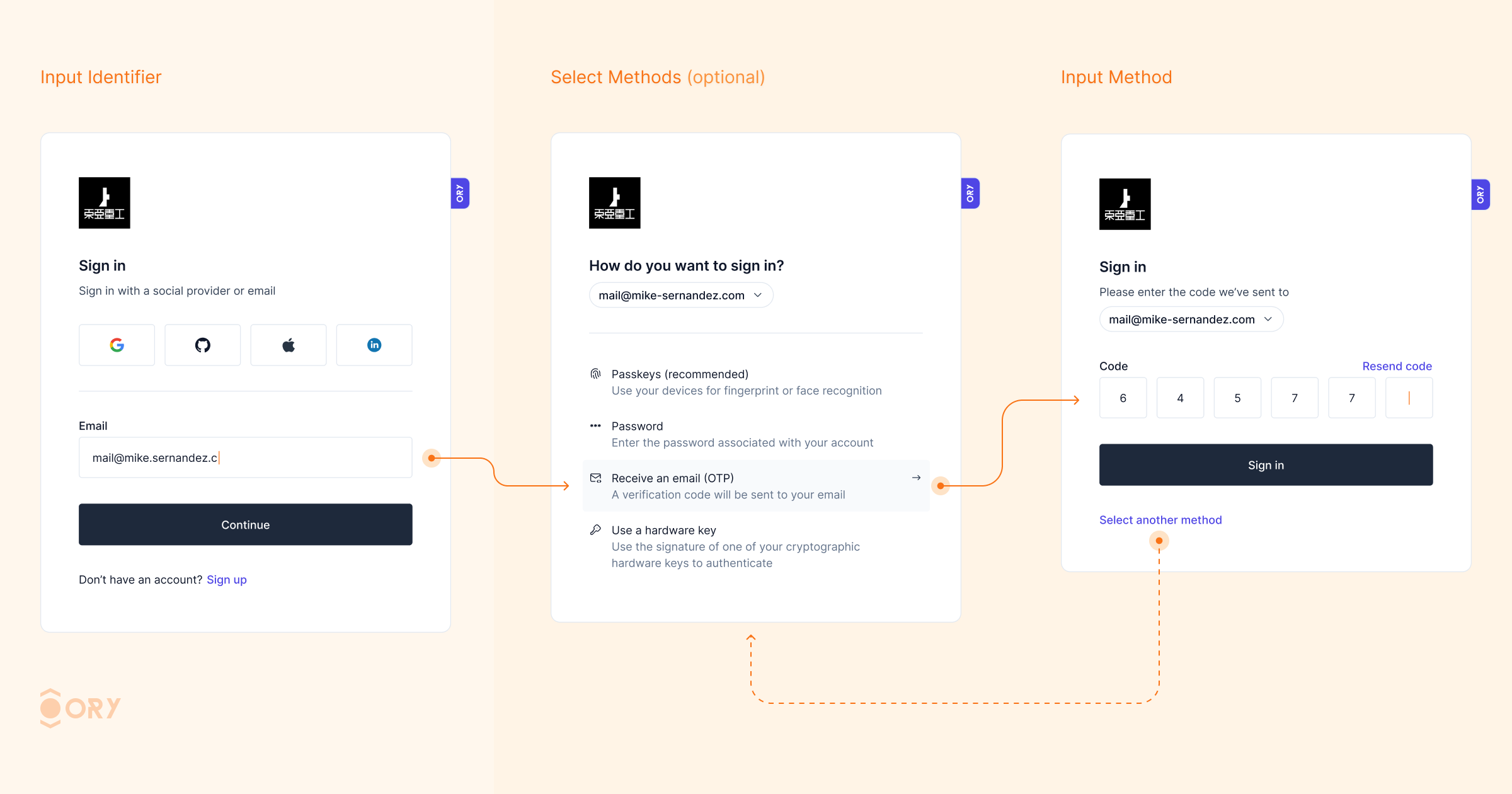
Enhance your sign-in experience with Identifier First Authentication. This feature allows users to first identify themselves (e.g., by providing their email or username) and then proceed with the chosen authentication method, whether it be OTP code, passkeys, passwords, or social login. By streamlining the sign-in process, users can select the authentication method that best suits their needs, reducing friction and enhancing security. Identifier First Authentication improves user flow and reduces the likelihood of errors, resulting in a more user-friendly and efficient login experience.
The UI for OpenID Connect (OIDC) account linking has been improved to provide better user guidance and error messages during the linking process. As a result, account linking error rates have dropped significantly, making it easier for users to link multiple identities (e.g., social login and email-based accounts) to the same profile. This improvement enhances user convenience, reduces support inquiries, and offers a seamless multi-account experience.
You can now use Salesforce as an identity provider, expanding the range of supported identity providers. This integration allows organizations already using Salesforce for identity management to leverage their existing infrastructure, simplifying user management and enhancing the authentication experience.
Social sign-in has been enhanced with better detection and handling of double-submit issues, especially for platforms like Facebook and Apple mobile login. These changes make the social login process more reliable, reducing errors and improving the user experience. Additionally, Ory Kratos now supports social providers in credential discovery, offering more flexibility during sign-up and sign-in flows.
One-Time Password (OTP) MFA has been improved with more robust handling of code-based authentication. The enhancements ensure a smoother flow when using OTP for multi-factor authentication (MFA), providing clearer guidance to users and improving fallback mechanisms. These updates help to prevent users from being locked out due to misconfigurations or errors during the MFA process, increasing security without compromising user convenience.
-
Deprecated
viaParameter for SMS 2FA: Theviaparameter is now deprecated when performing SMS 2FA. If not included, users will see all their phone/email addresses to perform the flow. This parameter will be removed in a future version. Ensure your identity schema has the appropriate code configuration for passwordless or 2FA login. -
Endpoint Change: The
/admin/session/.../extendendpoint will now return 204 No Content for new Ory Network projects. Returning 200 with the session body will be deprecated in future versions. -
SDK Enhancements: Added new methods and support for additional actions in the SDK, improving integration capabilities.
-
Password Migration Hook: Added a password migration hook to facilitate migrating passwords where the hash is unavailable, easing the transition to Ory Kratos.
-
Partially Failing Batch Inserts: When batch-inserting multiple identities, conflicts or validation errors of a subset of identities in the batch still allow the rest of the identities to be inserted. The returned JSON contains the error details that led to the failure.
-
Security Fixes: Fixed a security vulnerability where the
codemethod did not respect thehighest_availablesetting. Refer to the security advisory for more details. -
Session Extension Issues: Fixed issues related to session extension to prevent long response times on
/session/whoamiwhen extending sessions simultaneously. -
OIDC and Social Sign-In: Fixed UI and error handling for OpenID Connect and social sign-in flows, improving the overall experience.
-
Credential Identifier Handling: Corrected handling of code credential identifiers, ensuring proper detection of phone numbers and correct functioning of SMS/email MFA.
-
Concurrent Updates for Webhooks: Fixed concurrent map update issues for webhook headers, improving webhook reliability.
-
Passwordless & 2FA Login: Before upgrading, ensure your identity schema has the appropriate code configuration when using the code method for passwordless or 2FA login.
-
Code Method for 2FA: If you use the code method for 2FA or 1FA login but haven't configured the code identifier, set
selfservice.methods.code.config.missing_credential_fallback_enabledtotrueto avoid user lockouts.
We hope you enjoy the new features and improvements in Ory Kratos v1.3.0. Please remember to leave a GitHub star and check out our other open-source projects. Your feedback is valuable to us, so join the Ory community and help us shape the future of identity management.
Breaking Changes
When using two-step registration, it was previously possible to send method=profile:back to get to the previous screen. This feature was not documented in the SDK API yet. Going forward, please instead use screen=previous.
Please note that the via parameter is deprecated when performing SMS 2FA. It will be removed in a future version. If the parameter is not included in the request, the user will see all their phone/email addresses from which to perform the flow.
Before upgrading, ensure that your identity schema has the appropriate code configuration when using the code method for passwordless or 2fa login.
If you are using the code method for 2FA login already, or you are using it for 1FA login but have not yet configured the code identifier, set selfservice.methods.code.config.missing_credential_fallback_enabled to true to prevent users from being locked out.
Please note that the via parameter is deprecated when performing SMS 2FA. It will be removed in a future version. If the parameter is not included in the request, the user will see all their phone/email addresses from which to perform the flow.
Before upgrading, ensure that your identity schema has the appropriate code configuration when using the code method for passwordless or 2fa login.
If you are using the code method for 2FA login already, or you are using it for 1FA login but have not yet configured the code identifier, set selfservice.methods.code.config.missing_credential_fallback_enabled to true to prevent users from being locked out.
Going forward, the /admin/session/.../extend endpoint will return 204 no content for new Ory Network projects. We will deprecate returning 200 + session body in the future.
Bug Fixes
-
Add continue with only for json browser requests (#4002) (e0a4010)
-
Add fallback to providerLabel (#3999) (d26f204):
This adds a fallback to the provider label when trying to register a duplicate identifier with an oidc.
Current error message:
Signing in will link your account to "[email protected]" at provider "". If you do not wish to link that account, please start a new login flow.The label represents an optional label for the UI, but in my case it's always empty. I suggest we fallback to the provider when the label is not present. In case the label is present, the behaviour won't change.
Fallback to provider:
Signing in will link your account to "[email protected]" at provider "google". If you do not wish to link that account, please start a new login flow. -
Add missing JS triggers (7597bc6)
-
Do not populate
id_firstfirst step for account linking flows (#4074) (6ab2637) -
Emit SelfServiceMethodUsed in SettingsSucceeded event (#4056) (76af303)
-
Include duplicate credentials in account linking message (#4079) (122b63d)
-
Incorrect append of code credential identifier (#4102) (3215792), closes #4076
-
Move password migration hook config (#3986) (b5a66e0):
This moves the password migration hook to
selfservice: methods: password: config: migrate_hook: ...
-
Normalize code credentials and deprecate via parameter (c417b4a):
Before this, code credentials for passwordless and mfa login were incorrectly stored and normalized. This could cause issues where the system would not detect the user's phone number, and where SMS/email MFA would not properly work with the
highest_availablesetting. -
Passthrough correct organization ID to CompletedLoginForWithProvider (#4124) (ad1acd5)
-
Password migration hook config (#4001) (50deedf):
This fixes the config loading for the password migration hook.
-
Replace submit with continue button for recovery and verification and add maxlength (04850f4)
-
Return credentials in FindByCredentialsIdentifier (#4068) (f949173):
Instead of re-fetching the credentials later (expensive), we load them only once.
-
Return error if invalid UUID is supplied to ids filter (#4116) (98140f2)
-
security: Code credential does not respect
highest_availablesetting (b0111d4):This patch fixes a security vulnerability which prevents the
codemethod to properly report it's credentials count to thehighest_availablemechanism.For more details on this issue please refer to the security advisory.
-
Timestamp precision on mysql (9a1f171)
-
Transient_payload is lost when verification flow started as part of registration (#3983) (192f10f)
-
Trigger oidc web hook on sign in after registration (#4027) (ad5fb09)
-
Validate page tokens for better error codes (#4021) (32737dc)
Code Generation
- Pin v1.3.0 release commit (0a49fd0)
Documentation
- Add google to supported providers in ID Token doc strings (#4026) (955bd8f)
- Typo in changelog (c508980)
Features
-
Add additional messages (735fc5b)
-
Add browser return_to continue_with action (7b636d8)
-
Add if method to sdk (612e3bf)
-
Add redirect to continue_with for SPA flows (99c945c):
This patch adds the new
continue_withactionredirect_browser_to, which contains the redirect URL the app should redirect to. It is only supported for SPA (not server-side browser apps, not native apps) flows at this point in time. -
Add social providers to credential discovery as well (5f4a2bf)
-
Add support for Salesforce as identity provider (#4003) (3bf1ca9)
-
Allow deletion of an individual OIDC credential (#3968) (a43cef2):
This extends the existing
DELETE /admin/identities/{id}/credentials/{type}API to accept an?identifier=foobarquery parameter for{type}==oidclike such:DELETE /admin/identities/{id}/credentials/oidc?identifier=github%3A012345This will delete the GitHub OIDC credential with the identifier
github:012345(012345is the subject as returned by GitHub).To find out which OIDC credentials exist, call
GET /admin/identities/{id}?include_credential=oidcbeforehand.This will allow you to delete individual OIDC credentials for users even if they have several set up.
-
Allow partially failing batch inserts (#4083) (4ba7033):
When batch-inserting multiple identities, conflicts or validation errors of a subset of identities in the batch still allow the rest of the identities to be inserted. The returned JSON contains the error details that lead to the failure.
-
Better detection if credentials exist on identifier first login (#3963) (42ade94)
-
Change
method=profile:backtoscreen=previous(#4119) (2cd8483) -
Client-side PKCE take 3 (#4078) (f7c1024):
- feat: client-side PKCE
This change introduces a new configuration for OIDC providers: pkce with values auto (default), never, force.
When auto is specified or the field is omitted, Kratos will perform autodiscovery and perform PKCE when the server advertises support for it. This requires the issuer_url to be set for the provider.
never completely disables PKCE support. This is only theoretically useful: when a provider advertises PKCE support but doesn't actually implement it.
force always sends a PKCE challenge in the initial redirect URL, regardless of what the provider advertises. This setting is useful when the provider offers PKCE but doesn't advertise it in his ./well-known/openid-configuration.
Important: When setting pkce: force, you must whitelist a different return URL for your OAuth2 client in the provider's configuration. Instead of /self-service/methods/oidc/callback/, you must use /self-service/methods/oidc/callback (note missing last path segment). This is to enable the use of the same OAuth client ID+secret when configuring several Kratos OIDC providers, without having to whitelist individual redirect_uris for each Kratos provider config.
-
chore: regenerate SDK, bump DB versions, cleanup tool install
-
chore: get final organization ID from provider config during registration and login
-
chore: fixup OIDC function signatures and improve tests
-
Identifier first auth (1bdc19a)
-
Identifier first login for all first factor login methods (638b274)
-
Improve session extend performance (#3948) (4e3fad4):
This patch improves the performance for extending session lifespans. Lifespan extension is tricky as it is often part of the middleware of Ory Kratos consumers. As such, it is prone to transaction contention when we read and write to the same session row at the same time (and potentially multiple times).
To address this, we:
- Introduce a locking mechanism on the row to reduce transaction contention;
- Add a new feature flag that toggles returning 204 no content instead of 200 + session.
Be aware that all reads on the session table will have to wait for the transaction to commit before they return a value. This may cause long(er) response times on
/session/whoamifor sessions that are being extended at the same time. -
Password migration hook (#3978) (c9d5573):
This adds a password migration hook to easily migrate passwords for which we do not have the hash.
For each user that needs to be migrated to Ory Network, a new identity is created with a credential of type password with a config of {"use_password_migration_hook": true} .
When a user logs in, the credential identifier and password will be sent to the password_migration web hook if all of these are true:
The user’s identity’s password credential is {"use_password_migration_hook": true}
The password_migration hook is configured
After calling the password_migration hook, the HTTP status code will be inspected:
On 200, we parse the response as JSON and look for {"status": "password_match"}. The password credential config will be replaced with the hash of the actual password.
On any other status code, we assume that the password is not valid. -
sdk: Add missing profile discriminator to update registration (0150795)
-
sdk: Avoid eval with javascript triggers (dd6e53d):
Using
OnLoadTriggerandOnClickTriggerone can now map the trigger to the corresponding JavaScript function.For example, trigger
{"on_click_trigger":"oryWebAuthnRegistration"}should be translated towindow.oryWebAuthnRegistration():if (attrs.onClickTrigger) { window[attrs.onClickTrigger]() } -
Separate 2fa refresh from 1st factor refresh (#3961) (89355d8)
-
Set maxlength for totp input (51042d9)
Tests
- Add form hydration tests for code login (37781a9)
- Add form hydration tests for idfirst login (633b0ba)
- Add form hydration tests for oidc login (df0cdcb)
- Add form hydration tests for passkey login (a777854)
- Add form hydration tests for password login (7186e7e)
- Add form hydration tests for webauthn login (8b68163)
- Add tests for idfirst (5f76c15)
- Additional code credential test case (#4122) (4f2c854)
- Deflake and parallelize persister tests (#3953) (61f87d9)
- Deflake session extend config side-effect (#3950) (b192c92)
- Enable server-side config from context (#3954) (e0001b0)
- Improve stability of refresh test (#4037) (68693a4)
- Resolve CI failures (#4067) (dbf7274)
- Resolve issues and update snapshots for all selfservice strategies (e2e81ac)
- Update incorrect usage of Auth0 in Salesforce tests (#4007) (6ce3068)
- Verify redirect continue_with in hook executor for browser clients (7b0b94d)
Unclassified
-
Merge commit from fork (123e807):
- fix(security): code credential does not respect
highest_availablesetting
This patch fixes a security vulnerability which prevents the
codemethod to properly report it's credentials count to thehighest_availablemechanism.For more details on this issue please refer to the security advisory.
- fix: normalize code credentials and deprecate via parameter
Before this, code credentials for passwordless and mfa login were incorrectly stored and normalized. This could cause issues where the system would not detect the user's phone number, and where SMS/email MFA would not properly work with the
highest_availablesetting. - fix(security): code credential does not respect
-
Update .github/workflows/ci.yaml (2d60772)
Changelog
- 123e807 Merge commit from fork
- 2d60772 Update .github/workflows/ci.yaml
- 4e25ce9 autogen(docs): generate and bump docs
- 276fb51 autogen(docs): regenerate and update changelog
- 7840335 autogen(docs): regenerate and update changelog
- aa48c6b autogen(docs): regenerate and update changelog
- 4e2902c autogen(docs): regenerate and update changelog
- 4f4394c autogen(docs): regenerate and update changelog
- 5b251c0 autogen(docs): regenerate and update changelog
- 014be39 autogen(docs): regenerate and update changelog
- 2a6e220 autogen(docs): regenerate and update changelog
- 45bbec4 autogen(docs): regenerate and update changelog
- 1146599 autogen(docs): regenerate and update changelog
- 702e1e8 autogen(docs): regenerate and update changelog
- d72f456 autogen(docs): regenerate and update changelog
- ff90216 autogen(docs): regenerate and update changelog
- e451b74 autogen(docs): regenerate and update changelog
- 3db4256 autogen(docs): regenerate and update changelog
- 358521a autogen(docs): regenerate and update changelog
- 7674f46 autogen(docs): regenerate and update changelog
- 198e79b autogen(docs): regenerate and update changelog
- fa2da75 autogen(docs): regenerate and update changelog
- 7e7fdc2 autogen(docs): regenerate and update changelog
- 78bc473 autogen(docs): regenerate and update changelog
- def6225 autogen(docs): regenerate and update changelog
- 630c487 autogen(docs): regenerate and update changelog
- 4547e8b autogen(openapi): regenerate swagger spec and internal client
- 369aad4 autogen(openapi): regenerate swagger spec and internal client
- bcffb65 autogen(openapi): regenerate swagger spec and internal client
- 7f20adc autogen(openapi): regenerate swagger spec and internal client
- c910b4e autogen(openapi): regenerate swagger spec and internal client
- 7df3d56 autogen(openapi): regenerate swagger spec and internal client
- 020a9de autogen(openapi): regenerate swagger spec and internal client
- 8bd742f autogen(openapi): regenerate swagger spec and internal client
- b27e84b autogen(openapi): regenerate swagger spec and internal client
- b29dff3 autogen(openapi): regenerate swagger spec and internal client
- 278d8e0 autogen(openapi): regenerate swagger spec and internal client
- 30dd9c0 autogen(openapi): regenerate swagger spec and internal client
- bac030b autogen(openapi): regenerate swagger spec and internal client
- 1d9ef41 autogen(openapi): regenerate swagger spec and internal client
- ba0f30d autogen: add v1.2.0 to version.schema.json
- 0a49fd0 autogen: pin v1.3.0 release commit
- 72aae5b autogen: pin v1.3.0-pre.0 release commit
- de70e43 chore(deps): bump body-parser and express in /test/e2e/proxy (#4093)
- 74fd787 chore(deps): bump express from 4.18.2 to 4.20.0 in /test/e2e/proxy (#4095)
- ba2aac5 chore(deps): bump github.com/opencontainers/runc from 1.1.13 to 1.1.14 (#4075)
- 7d6a458 chore(deps): bump serve-static and express in /test/e2e/proxy (#4091)
- 0213ed9 chore: add kubescape image scanner (#3947)
- dbe9d10 chore: add missing text message fields (#4066)
- 4fb28b3 chore: align internal SDK with published SDK (#4019)
- 6129ec8 chore: bump dependencies (#4017)
- 54cb464 chore: don't return allowed return URLs (#4044)
- a84fb3f chore: improve courier logging (#3985)
- 5830ffb chore: improve tracing for selfservice strategies (#4061)
- 1bc4dc5 chore: move b2b config to selfservice section (#3949)
- f125f7f chore: re-add WithIdentifier (#3992)
- 9aefc0a chore: refactor API in package cipher for easier dependency injection (#4103)
- 5d8e327 chore: regenerate SDK
- 4ace176 chore: regenerate SDK and format code
- 3260550 chore: regenerate config types
- 2ad0ed9 chore: remove max length
- b7102c8 chore: rename one_step to unified
- 0dec428 chore: sdk+ci (#4088)
- 5592029 chore: update CI, dependencies, and some inaccurate assertions (#4085)
- 671368d chore: update newsletter link (#4011)
- 9894d0a chore: update repository templates to ory/meta@297c8a5
- 9001c44 chore: update repository templates to ory/meta@3cf0f00
- 5d372a3 chore: update repository templates to ory/meta@4132def
- b0a8a3b chore: update repository templates to ory/meta@939b80f
- 5c650ce chore: update repository templates to ory/meta@95e82c6
- 7945104 chore: update repository templates to ory/meta@fe4ffe0
- 2800fcd chore: updated snapshots and clean up
- f7c38f0 chore: upgrade dockertest to address cve (#4038)
- aa7f958 chore: upgrade goreleaser to v2 (#4123)
- a702fdf chore: use correct import
- 180287a chore: use label in link/unlink settings nodes (#3977)
- e3f1da0 deps: update Code QL action to v2 (#4008)
- 955bd8f docs: add google to supported providers in ID Token doc strings (#4026)
- c508980 docs: typo in changelog
- 0150795 feat(sdk): add missing profile discriminator to update registration
- dd6e53d feat(sdk): avoid eval with javascript triggers
- 735fc5b feat: add additional messages
- 7b636d8 feat: add browser return_to continue_with action
- 612e3bf feat: add if method to sdk
- 99c945c feat: add redirect to continue_with for SPA flows
- 5f4a2bf feat: add social providers to credential discovery as well
- 3bf1ca9 feat: add support for Salesforce as identity provider (#4003)
- 8225e40 feat: add tests for two step login (#3959)
- a43cef2 feat: allow deletion of an individual OIDC credential (#3968)
- 4ba7033 feat: allow partially failing batch inserts (#4083)
- 42ade94 feat: better detection if credentials exist on identifier first login (#3963)
- 2cd8483 feat: change
method=profile:backtoscreen=previous(#4119) - af5ea35 feat: clarify session extend behavior (#3962)
- f7c1024 feat: client-side PKCE take 3 (#4078)
- 20156f6 feat: emit events in identity persister (#4107)
- eb97243 feat: enable new-style OIDC state generation (#4121)
- 1bdc19a feat: identifier first auth
- 638b274 feat: identifier first login for all first factor login methods
- 4e3fad4 feat: improve session extend performance (#3948)
- c9d5573 feat: password migration hook (#3978)
- 89355d8 feat: separate 2fa refresh from 1st factor refresh (#3961)
- 51042d9 feat: set maxlength for totp input
- b0111d4 fix(security): code credential does not respect
highest_availablesetting - 2c7ff3c fix: add PKCE config key to config schema (#4098)
- e0a4010 fix: add continue with only for json browser requests (#4002)
- d26f204 fix: add fallback to providerLabel (#3999)
- 7597bc6 fix: add missing JS triggers
- 340f698 fix: batch identity created event (#4111)
- 6ceb2f1 fix: concurrent map update for webhook header (#4055)
- 6ab2637 fix: do not populate
id_firstfirst step for account linking flows (#4074) - 4d1954a fix: downgrade go-webauthn (#4035)
- 76af303 fix: emit SelfServiceMethodUsed in SettingsSucceeded event (#4056)
- ddb838e fix: filter web hook headers (#4048)
- 2b4a618 fix: improve OIDC account linking UI (#4036)
- 122b63d fix: include duplicate credentials in account linking message (#4079)
- 3215792 fix: incorrect append of code credential identifier (#4102)
- 7c5299f fix: jsonnet timeouts (#3979)
- b5a66e0 fix: move password migration hook config (#3986)
- c417b4a fix: normalize code credentials and deprecate via parameter
- ad1acd5 fix: passthrough correct organization ID to CompletedLoginForWithProvider (#4124)
- 50deedf fix: password migration hook config (#4001)
- 6016cc8 fix: pw migration param (#3998)
- 81bc152 fix: refactor internal API to prevent panics (#4028)
- 310a405 fix: remove flows from log messages (#3913)
- 04850f4 fix: replace submit with continue button for recovery and verification and add maxlength
- f949173 fix: return credentials in FindByCredentialsIdentifier (#4068)
- 98140f2 fix: return error if invalid UUID is supplied to ids filter (#4116)
- 9a1f171 fix: timestamp precision on mysql
- 192f10f fix: transient_payload is lost when verification flow started as part of registration (#3983)
- ad5fb09 fix: trigger oidc web hook on sign in after registration (#4027)
- 8350625 fix: typo in login link CLI error messages (#3995)
- 32737dc fix: validate page tokens for better error codes (#4021)
- ff6ed5b fix: whoami latency (#4070)
- 37781a9 test: add form hydration tests for code login
- 633b0ba test: add form hydration tests for idfirst login
- df0cdcb test: add form hydration tests for oidc login
- a777854 test: add form hydration tests for passkey login
- 7186e7e test: add form hydration tests for password login
- 8b68163 test: add form hydration tests for webauthn login
- 5f76c15 test: add tests for idfirst
- 4f2c854 test: additional code credential test case (#4122)
- 61f87d9 test: deflake and parallelize persister tests (#3953)
- b192c92 test: deflake session extend config side-effect (#3950)
- e0001b0 test: enable server-side config from context (#3954)
- 68693a4 test: improve stability of refresh test (#4037)
- dbf7274 test: resolve CI failures (#4067)
- e2e81ac test: resolve issues and update snapshots for all selfservice strategies
- 6ce3068 test: update incorrect usage of Auth0 in Salesforce tests (#4007)
- 7b0b94d test: verify redirect continue_with in hook executor for browser clients
Artifacts can be verified with cosign using this public key.