v1.2.0
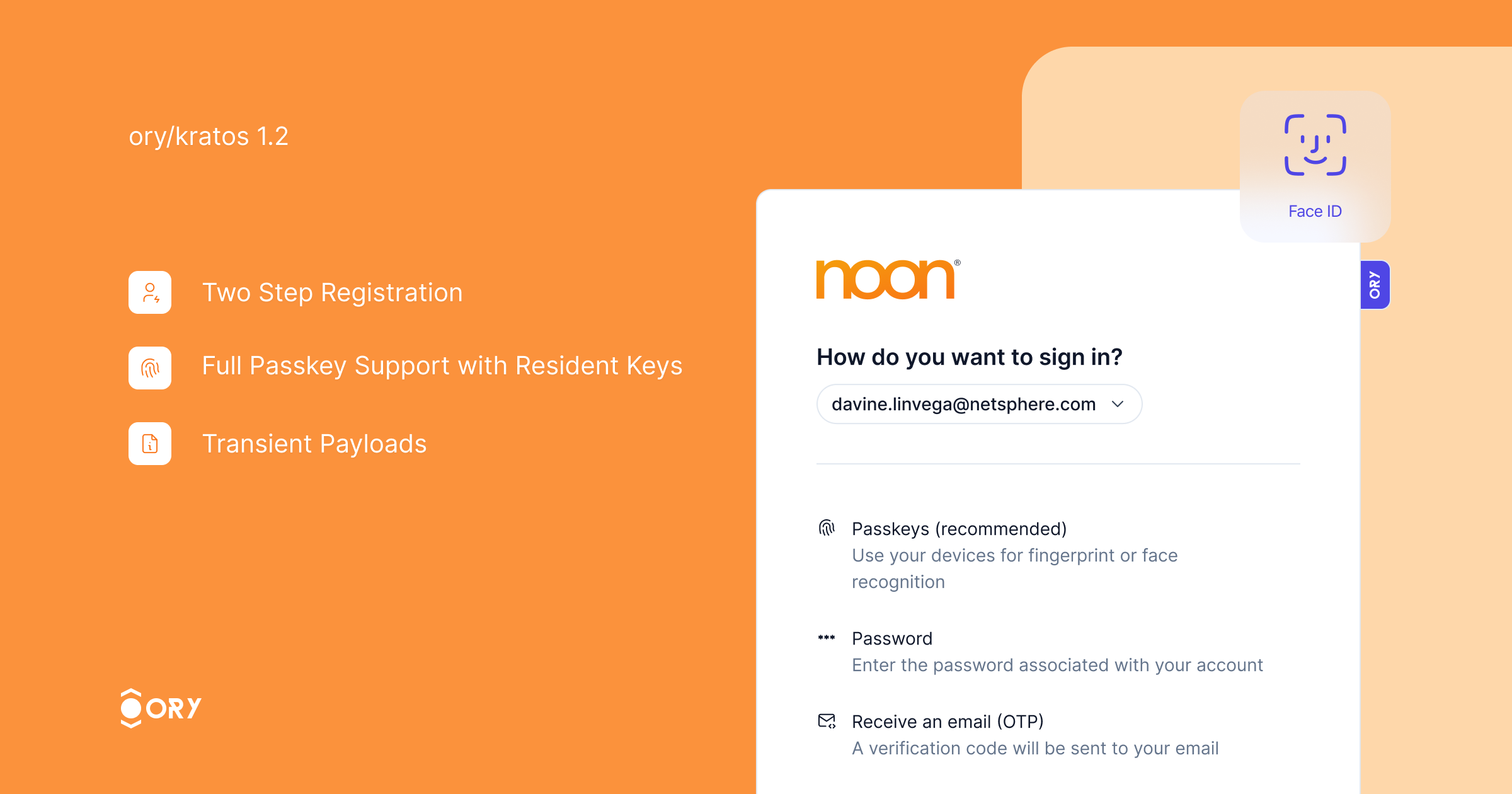
Ory Kratos v1.2 is the most complete, scalable, and secure open-source identity server available. We are thrilled to announce its release!
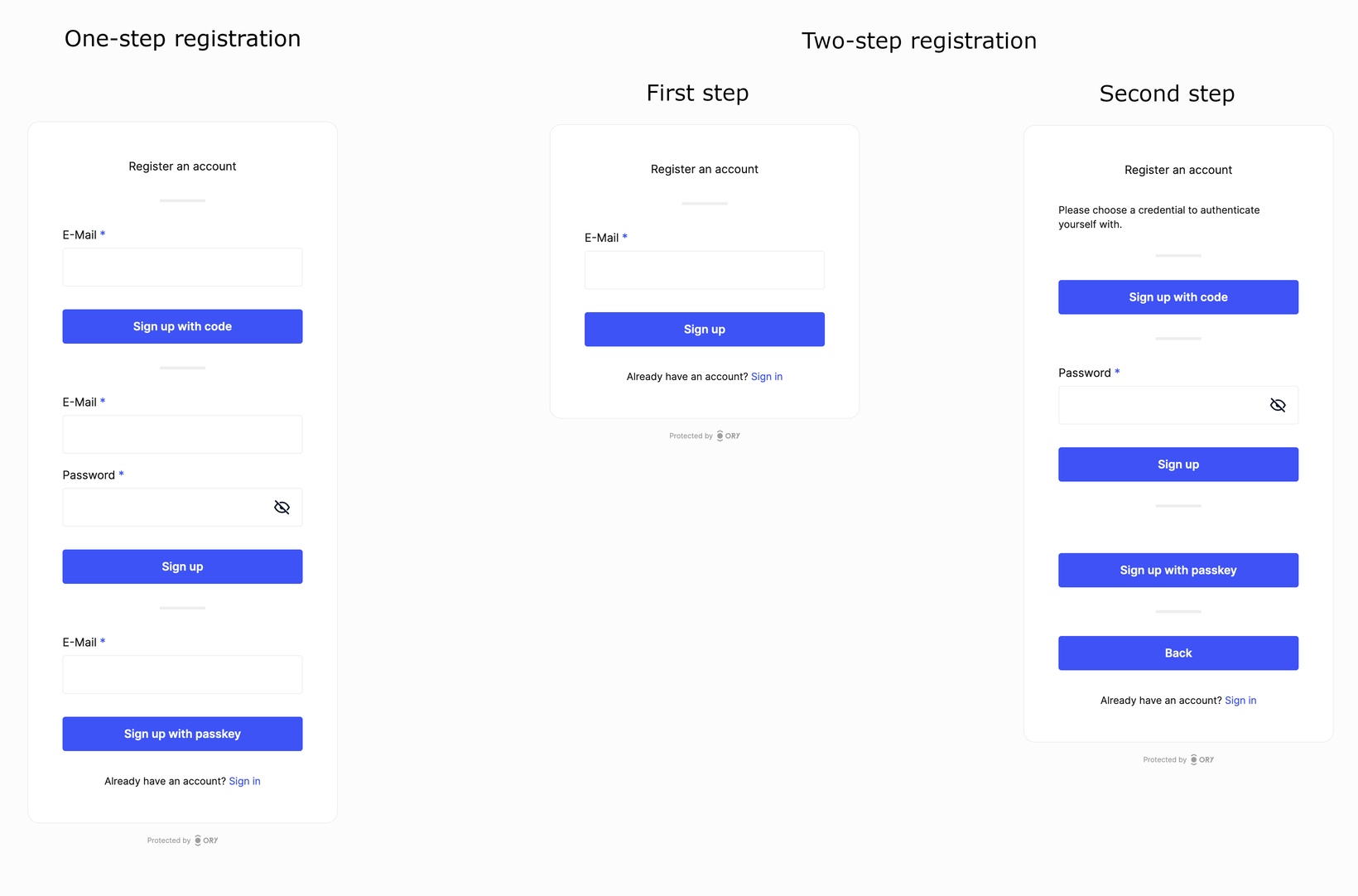
This release introduces two major features: two-step registration and full PassKey with resident key support.
Passkeys provide a secure and convenient authentication method, eliminating the need for passwords while ensuring strong security. With this release, we have added support for resident keys, enabling offline authentication. Credential discovery allows users to link existing passkeys to their Ory account seamlessly.
passkeys.webm
Two-step registration improves the user experience by dividing the registration process into two steps. Users first enter their identity traits, and then choose a credential method for authentication, resulting in a streamlined process. This feature is especially useful when enabling multiple authentication strategies, as it eliminates the need to repeat identity traits for each strategy.
The 107 commits since v1.1 include several improvements:
- Webhooks now carry session information if available.
- Transient Payloads are now available across all self-service flows.
- Sign in with Twitter is now available.
- Sign in with LinkedIn now includes an additional v2 provider compatible with LinkedIn's new SSO API.
- Two-Step Registration: An improved registration experience that separates entering profile information from choosing authentication methods.
- User Credentials Meta-Information can now be included on the list endpoint.
- Social Sign-In is now resilient to double-submit issues common with Facebook and Apple mobile login.
Two-Step Registration Enabled by Default: This is now the default setting. To disable, set selfservice.flows.registration.enable_legacy_one_step to true.
- Improved account linking and credential discovery during sign-up.
- The
return_toparameter is now respected in OIDC API flows. - Adjustments to database indices.
- Enhanced error messages for security violations.
- Improved SDK types.
- The
verificationandverification_uihooks are now available in the login flow. - Webhooks now contain the correct identity state in the after-verification hook chain.
We are doing this survey to find out how we can support self-hosted Ory users better. We strive to provide you with the best product and service possible and your feedback will help us understand what we're doing well and where we can improve to better meet your needs. We truly value your opinion and thank you in advance for taking the time to share your thoughts with us!
Fill out the survey now!
Breaking Changes
This feature enables two-step registration per default. Two-step registration is a significantly improved sign up flow and recommended when using more than one sign up methods. To disable two-step registration, set selfservice.flows.registration.enable_legacy_one_step to true. This value defaults to false.
Bug Fixes
-
Add login succeeded event to post registration hook (#3739) (b685fa5)
-
Add missing env vars to set up guide (#3855) (da90502):
Closes #3828
-
Add missing indexes and remove unused index (6d7372e)
-
Add missing indexes and remove unused index (#3756) (c905f02)
-
Allow updating just the verified_at timestamp of addresses (#3880) (696cc1b)
-
Always issue session last (#3876) (e942507):
In post persist hooks, the session issuance hook always needs
to come last. This fixes the getHooks function to ensure this. -
Db index and duplicate credentials error (#3896) (9f34a21):
- fix: don't return password cred type if empty
- fix: better index for config.user_handle on identity_credentials
-
Do not require method to be passkey in settings schema (#3862) (660f330)
-
Execute verification & verification_ui properly in login flows (#3847) (5aad1c1)
-
Ignore decrypt errors in WithDeclassifiedCredentials (#3731) (8f5192f)
-
Include all creds in duplicate credential err (#3881) (e06c241)
-
Make sure emails can still be sent with SMS enabled (#3795) (7c68c5a)
-
oidc: Grace period for continuity container on oidc callbacks (#3915) (1a9a096)
-
Respect return_to in OIDC API flow error case (#3893) (e8f1bcb):
- fix: respect return_to in OIDC API flow error case
This fix ensures that we redirect the user to the return_to URL
when an error occurs during the OIDC login for native flows.Native flows are initialized through the API, and the browser
URL is retrieved from a 422 response after a POST to submit the
login flow. Successful OIDC flows already returned thecodeto
thereturn_toURL. Now, unsuccessful flows return theflowwith
the current flow ID (which might have changed), so that the caller
can retrieve the full flow and act accordingly.- fix: ignore trivvy CVE report
Bump in distroless is still open
-
sdk: Expand identity in session extension (#3843) (04f0231), closes #3842
-
sdk: Improve discriminators for node and Go (#3821) (9ddf7cc)
-
Test assertions on declassifying OIDC tokens (#3773) (7f8a7f1)
-
Tolerate more "truthy" values when creating new flows (#3841) (49d93c0), closes #3839:
Use strconv.ParseBool to accept multiple "truthy" values for the
refreshandreturn_session_token_exchange_codequery parameters when
creating a new login flow.For some SDKs (e.g.: Python), these stringification of booleans is not
user-controlled and these endpoints could not be used fully due to the
backend ignoring any value other thantrue(all lowercase). -
Use correct post-verification identity state in post-hooks (#3863) (6e63d06)
-
Webhook transient payload in OIDC login flows (#3857) (2cdfc70):
- fix: transient payload with OIDC login
Code Generation
- Pin v1.2.0 release commit (1a70648)
Documentation
Features
-
Add
include_credentialquery param to/admin/identitieslist call (#3343) (d94530a) -
Allow admin to create API code recovery flows (#3939) (25d1ecd)
-
Linkedin v2 provider (#3804) (a6ad983):
-
feat: add linkedin-v2 provider
-
docs: document linkedin special-case
-
-
PassKeys with Resident Keys and two-step registration (#3748) (3621411)
-
Use authenticate endpoint for x (#3833) (3d9ba5d):
Improves the "Log in with X" experience by not asking the user to re-authenticate every time.
Tests
-
Resolve flaky e2e tests (#3935) (a14927d):
-
test: resolve flaky code registration tests
-
chore: don't fail logout if cookie is not found
-
chore: remove .only
-
chore: reduce wait
-
chore: u
-
chore: u
-
chore: u
-
Unclassified
Changelog
- 087748c Remove unnecessary COPY command from Dockerfile (#3771)
- d755fbb autogen(docs): generate and bump docs
- b96c6a5 autogen(docs): regenerate and update changelog
- f8fbb00 autogen(docs): regenerate and update changelog
- bdf992e autogen(docs): regenerate and update changelog
- b7fd23b autogen(docs): regenerate and update changelog
- 0f81b76 autogen(docs): regenerate and update changelog
- f696fcf autogen(docs): regenerate and update changelog
- 34399c2 autogen(docs): regenerate and update changelog
- ecbd1e3 autogen(docs): regenerate and update changelog
- 41310b3 autogen(docs): regenerate and update changelog
- fa5a112 autogen(docs): regenerate and update changelog
- 9fa25b5 autogen(docs): regenerate and update changelog
- dfc931f autogen(docs): regenerate and update changelog
- 31f77b8 autogen(docs): regenerate and update changelog
- ddbea20 autogen(docs): regenerate and update changelog
- 9c69ef2 autogen(docs): regenerate and update changelog
- 9710549 autogen(docs): regenerate and update changelog
- 264395a autogen(docs): regenerate and update changelog
- cd92f2a autogen(docs): regenerate and update changelog
- a1bf427 autogen(docs): regenerate and update changelog
- 7f1fd81 autogen(openapi): regenerate swagger spec and internal client
- 60537a9 autogen(openapi): regenerate swagger spec and internal client
- da6b38a autogen(openapi): regenerate swagger spec and internal client
- b7e5144 autogen(openapi): regenerate swagger spec and internal client
- ec90929 autogen(openapi): regenerate swagger spec and internal client
- ab8e1b5 autogen(openapi): regenerate swagger spec and internal client
- 718cb7c autogen(openapi): regenerate swagger spec and internal client
- 0b6f91e autogen(openapi): regenerate swagger spec and internal client
- fa806aa autogen(openapi): regenerate swagger spec and internal client
- 3c06689 autogen(openapi): regenerate swagger spec and internal client
- 473e17c autogen(openapi): regenerate swagger spec and internal client
- 8ebdfd2 autogen(openapi): regenerate swagger spec and internal client
- 644e669 autogen(openapi): regenerate swagger spec and internal client
- b132c94 autogen(openapi): regenerate swagger spec and internal client
- 1459403 autogen(openapi): regenerate swagger spec and internal client
- dee5844 autogen(openapi): regenerate swagger spec and internal client
- 037bdf8 autogen(openapi): regenerate swagger spec and internal client
- d9dbaad autogen(openapi): regenerate swagger spec and internal client
- b47554b autogen(openapi): regenerate swagger spec and internal client
- eb67bed autogen(openapi): regenerate swagger spec and internal client
- 5dcbb77 autogen(openapi): regenerate swagger spec and internal client
- ca7cd23 autogen(openapi): regenerate swagger spec and internal client
- 6638c3e autogen: add v1.1.0 to version.schema.json
- 1a70648 autogen: pin v1.2.0 release commit
- 2baecae autogen: pin v1.2.0-pre.0 release commit
- 49e1a39 chore(deps): bump github.com/go-jose/go-jose/v3 from 3.0.1 to 3.0.3 (#3805)
- 0f3d082 chore(deps): bump github.com/lestrrat-go/jwx from 1.2.28 to 1.2.29 (#3812)
- 83792ef chore: allow smtp jim config (#3932)
- 3ecdf2b chore: fix function name in comment (#3869)
- fbbac77 chore: improve courier logging (#3943)
- 5288bc7 chore: make identity schema provider a proper service (#3908)
- 63ce470 chore: remove e2e playwright env (#3794)
- 17f9a4f chore: render CLI doc messages into their own *.md file in docs (#3886)
- de8e59c chore: update repository templates to ory/meta@e838bee
- 050a4dc chore: upgrade nyaruka/phonenumbers to v1.3.6 (#3940)
- 0713e2d chore: upgrade ory/x to v0.0.619 (#3845)
- cd01cb9 docs: remove delete reference from batch patch identity (#3906)
- 3621411 feat: PassKeys with Resident Keys and two-step registration (#3748)
- d94530a feat: add
include_credentialquery param to/admin/identitieslist call (#3343) - 4642de0 feat: add headers to web hooks (#3849)
- 386078e feat: add session to post login webhook (#3877)
- b8b747b feat: add transient payloads to all flows (#3738)
- 930fb19 feat: add twitter SSO (#3778)
- 43e4ead feat: add verification hook to login flow (#3829)
- 25d1ecd feat: allow admin to create API code recovery flows (#3939)
- c9dcce5 feat: control edge cache ttl (#3808)
- a6ad983 feat: linkedin v2 provider (#3804)
- 04390be feat: send OIDC claim keys to tracing (#3798)
- 3d9ba5d feat: use authenticate endpoint for x (#3833)
- 1a9a096 fix(oidc): grace period for continuity container on oidc callbacks (#3915)
- 04f0231 fix(sdk): expand identity in session extension (#3843)
- 9ddf7cc fix(sdk): improve discriminators for node and Go (#3821)
- e5d3b0a fix: CVEs in dependencies (#3902)
- b685fa5 fix: add login succeeded event to post registration hook (#3739)
- da90502 fix: add missing env vars to set up guide (#3855)
- 6d7372e fix: add missing indexes and remove unused index
- c905f02 fix: add missing indexes and remove unused index (#3756)
- b291c95 fix: add sms mfa via parameter to spec (#3766)
- 696cc1b fix: allow updating just the verified_at timestamp of addresses (#3880)
- e942507 fix: always issue session last (#3876)
- 7017490 fix: audit issues (#3797)
- 9730e09 fix: change return urls in quickstarts (#3928)
- cc39f8d fix: close res body (#3870)
- 9f34a21 fix: db index and duplicate credentials error (#3896)
- 660f330 fix: do not require method to be passkey in settings schema (#3862)
- 800f8f1 fix: don't require connection_uri in SMTP (#3861)
- 8eee972 fix: don't treat passkeys as AAL2 (#3853)
- ad0619d fix: drop index if exists (#3846)
- 8f8fd90 fix: drop trigram index on identifiers (#3827)
- 63d785e fix: enum type of session expandables (#3891)
- c435727 fix: enum type of session expandables (#3895)
- 5aad1c1 fix: execute verification & verification_ui properly in login flows (#3847)
- 8f5192f fix: ignore decrypt errors in WithDeclassifiedCredentials (#3731)
- c08b3ad fix: improve SDK discriminators (#3844)
- e06c241 fix: include all creds in duplicate credential err (#3881)
- 11d221a fix: linkedin issuer override (#3875)
- 7c68c5a fix: make sure emails can still be sent with SMS enabled (#3795)
- 0b32ce1 fix: missing indices and foreign keys (#3800)
- d01b670 fix: passing transient payloads (#3838)
- c5f39f4 fix: prevent SMTP URL leak on unparsable URL (#3770)
- e8f1bcb fix: respect return_to in OIDC API flow error case (#3893)
- e6db689 fix: show error page on identity mismatch (#3790)
- 7f8a7f1 fix: test assertions on declassifying OIDC tokens (#3773)
- 49d93c0 fix: tolerate more "truthy" values when creating new flows (#3841)
- da51dcd fix: tweaks to UpsertSessions (#3878)
- 6e63d06 fix: use correct post-verification identity state in post-hooks (#3863)
- 2cdfc70 fix: webhook transient payload in OIDC login flows (#3857)
- 6b275f3 test: deflake session test (#3864)
- 7277368 test: resolve failing test for empty tokens (#3775)
- a14927d test: resolve flaky e2e tests (#3935)
Artifacts can be verified with cosign using this public key.