Next PGP is an elegant, powerful, and modern Progressive Web App (PWA) built with Next.js. It provides an app like experience for generating keys, managing keyrings, and securely encrypting and decrypting messages with ease.
- Key Generation:
- Effortlessly generate secure PGP keys
- Supports multiple algorithms, including:
- Curve25519 (EdDSA/ECDH) - Recommended
- NIST P-256, P-521 (ECDSA/ECDH)
- Brainpool P-256r1, P-512r1 (ECDSA/ECDH)
- RSA 2048, 3072, 4096
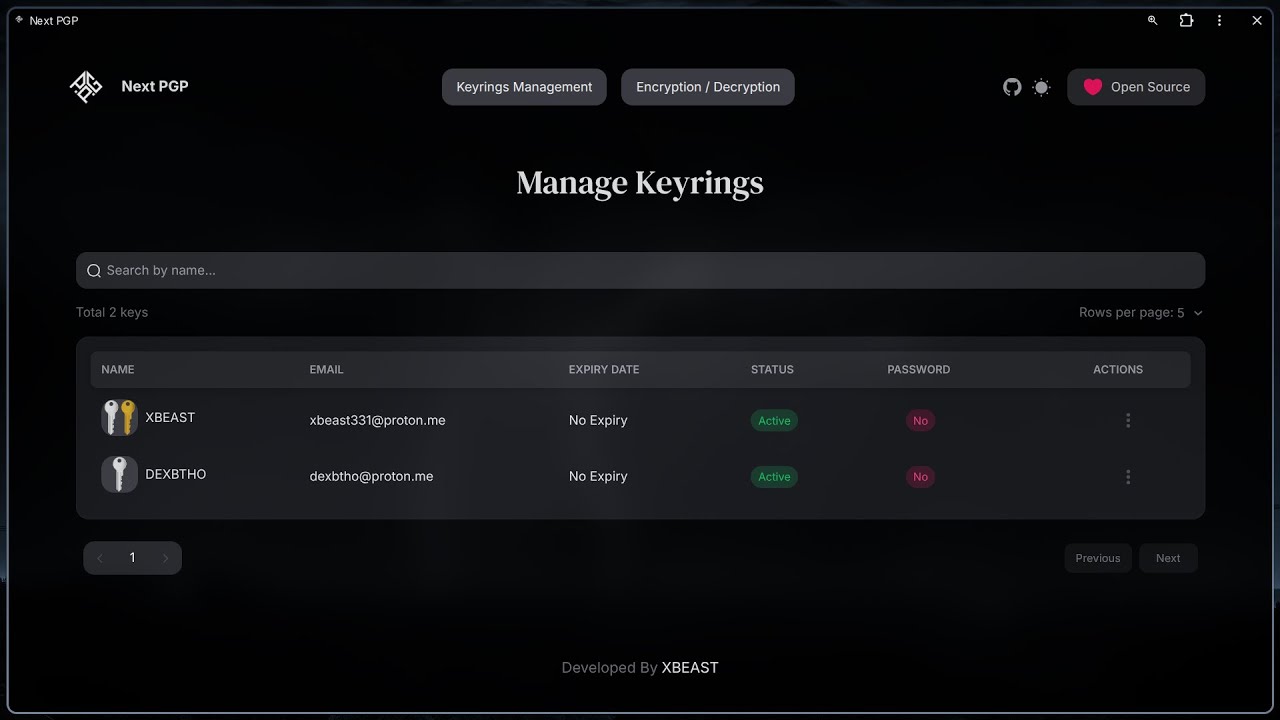
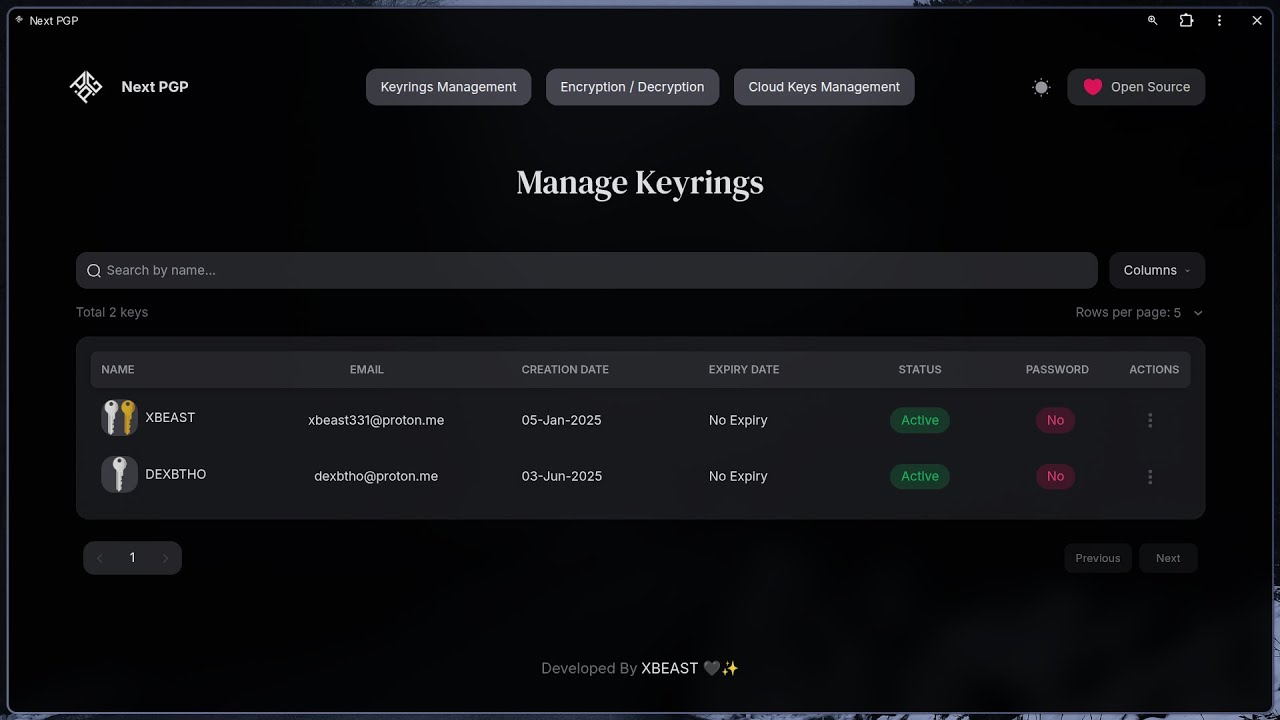
- Keyring Management:
- Add, manage, delete, import, export, and backup keys
- Search, import, and publish public keys via PGP keyservers
- Add, change, and remove passphrases
- Add, manage, and revoke User IDs
- Add, manage, and revoke subkeys
- Encryption & Decryption:
- Encrypt and decrypt messages with ease
- Secure file encryption and decryption
- Intuitive user interface for seamless operation
- Batch File Encryption & Decryption:
- Encrypt multiple files at once
- Decrypt multiple files efficiently
- Folder Encryption & Decryption:
- Encrypt and decrypt entire folders recursively
- Maintain original directory structure
- Cloud Management:
- Securely backup PGP keys to the cloud
- Manage keys remotely with encrypted vaults
- Ensure top-tier protection with end-to-end encryption
- Encrypted Vaults:
- Password-derived key security using PBKDF2 (1,000,000 iterations, SHA-512)
- Vault data including verification cipher encrypted client-side
- Strong confidentiality and integrity with AES-256-GCM
- Web Worker Multithreading:
- Dynamically scales encryption and decryption workloads in parallel across all CPU cores
- Keeps the interface fast and responsive, even during heavy processing
- Automatically adapts to your device's performance capabilities
- Secure Local Storage: Utilizes IndexedDB to store keys locally, encrypted by the Web Crypto API.
- Modern UI: Clean and elegant user experience built on modern design principles.
- Blazing Fast Performance: Built with Next.js to deliver superior speed and performance.
- Smooth Cloud Management: Seamless and secure integration of cloud based key storage and retrieval for enhanced accessibility and control.
- Cross Platform Progressive Web App (PWA): Web based application that works on every device — Windows, macOS, Linux, Android, and iOS with offline capabilities.
- Framework: Next JS
- UI Components: Hero UI
- Database: MongoDB for cloud storage and user vault management.
- PWA Integration: Service workers, manifest setup, and offline support.
- State Management: Efficient handling of state for keyrings and messages.
- Performance Optimization: Dynamic Web Worker pool for parallel cryptographic operations using all available CPU cores
Next PGP is built around a Zero-Knowledge and End-to-End Encryption (E2EE) model — ensuring that your secrets stay yours, even in the cloud.
- True End-to-End Encryption (E2EE): All encryption and decryption happens entirely on the client-side. Your PGP keys, vault contents, and sensitive data are encrypted before ever leaving your device — the server never sees them unencrypted.
- Vault Protection: Your vault password is used to derive an encryption key via PBKDF2 (with 1,000,000 iterations) on the client, securing your data with AES-256-GCM. For authentication, the password verification is also handled client-side ensuring zero-knowledge architecture at every layer.
- Zero-knowledge cloud storage: Although you can back up and sync your encrypted vault to the cloud, it is fully opaque to the server. Only you can decrypt it.
- In-memory vault context: Vault password is never stored in session or local storage — it's kept in memory only while the app is open, adding an additional layer of runtime safety.
- Built on HTTPS + Web Crypto API: Communication is always encrypted in transit, and cryptographic operations use trusted, native browser APIs.
├─ User sets app password
├─ Generate 16-byte random salt
├─ Derive 32-byte key from password + salt using PBKDF2-SHA256 (1,000,000 iterations)
├─ Get or generate main encryption key (AES-GCM 256-bit)
├─ Export main crypto key to raw bytes
├─ Encrypt main crypto key with password-derived key:
│ ├─ Generate 12-byte random IV
│ ├─ Encrypt main crypto key bytes with AES-GCM + IV
│ └─ Store encrypted main crypto key + IV + salt + password hash
├─ Generate password hash for verification (SHA-256)
├─ Store in IndexedDB:
│ ├─ encrypted: encrypted main crypto key bytes
│ ├─ iv: 12-byte IV
│ ├─ salt: 16-byte salt
│ ├─ passwordHash: SHA-256 hash of password
│ └─ isPasswordProtected: true
└─ Store decrypted main crypto key in memory (encrypted with temporary key)
├─ User enters app password
├─ Fetch encrypted main crypto key record from IndexedDB
├─ Validate password protection is enabled
├─ Derive 32-byte key from password + stored salt using PBKDF2-SHA256 (1M iterations)
├─ Decrypt main crypto key:
│ ├─ Use derived key + stored IV
│ ├─ Decrypt encrypted main crypto key bytes with AES-GCM
│ └─ Import decrypted bytes as AES-GCM key
├─ Verify password by checking if decryption succeeds
│ ├─ If successful → correct password → unlock app
│ └─ If fails → incorrect password → show error
├─ Store decrypted main crypto key in memory:
│ ├─ Generate temporary AES-GCM key
│ ├─ Encrypt decrypted main crypto key with temporary key
│ ├─ Store encrypted main crypto key + IV + temp key in memory
│ └─ Set session flag in sessionStorage
└─ App is now unlocked and can access PGP keys
├─ User removes password protection
├─ Verify current password (requires decrypted main crypto key in memory)
├─ Generate new unencrypted main crypto key (AES-GCM 256-bit)
├─ Re-encrypt all PGP keys:
│ ├─ Decrypt each PGP key with old main crypto key
│ ├─ Re-encrypt with new main crypto key + random IV
│ └─ Update IndexedDB with new encrypted data
├─ Store new unencrypted main crypto key in IndexedDB:
│ ├─ key: raw main crypto key bytes
│ └─ isPasswordProtected: false
└─ Clear password protection completely
├─ Temporary session validation
├─ Auto-clear on page refresh
├─ Generate temporary AES-GCM key for memory storage
├─ Re-encrypt decrypted main crypto key with temporary key
├─ Store in memory (encrypted)
└─ No persistent sessions
├─ PGP keys encrypted with AES-GCM + random IV
├─ IndexedDB encryption with main crypto key
└─ Zero-knowledge architecture (client-side only)
├─ Web Crypto API for all operations
├─ HTTPS enforcement
├─ AES-GCM encryption for data protection
└─ PBKDF2 key derivation for password protection
├─ User enters password
├─ Generate 32-byte random verification text (Uint8Array)
├─ Convert to hex string and add "VERIFY:" prefix
├─ Encrypt verification text with password:
│ ├─ Generate 16-byte random salt
│ ├─ Generate 12-byte random IV
│ ├─ Derive 64-byte key from password + salt using PBKDF2-SHA512 (1,000,000 iterations)
│ │ ├─ First 32 bytes: AES-GCM key
│ │ └─ Next 32 bytes: HMAC-SHA256 key
│ ├─ Compress plaintext using DEFLATE (pako)
│ ├─ Encrypt compressed data with AES-GCM
│ ├─ Construct 45-byte header:
│ │ ├─ 2 bytes: MAGIC ('NP')
│ │ ├─ 1 byte: ENCRYPTION_VERSION
│ │ ├─ 1 byte: PURPOSE
│ │ ├─ 1 byte: KDF_ID (0x01 = PBKDF2)
│ │ ├─ 1 byte: CIPHER_ID (0x01 = AES-GCM)
│ │ ├─ 1 byte: FLAGS (0x01 = compression enabled)
│ │ ├─ 4 bytes: ITERATIONS (big-endian uint32)
│ │ ├─ 2 bytes: RESERVED (0x0000)
│ │ └─ 32 bytes: SHA-256 hash of header prefix (integrity)
│ ├─ Generate HMAC-SHA256 of (header + ciphertext + IV + salt)
│ ├─ Concatenate:
│ │ ├─ header (45 bytes)
│ │ ├─ ciphertext
│ │ ├─ IV (12 bytes)
│ │ ├─ salt (16 bytes)
│ │ └─ HMAC (32 bytes)
│ └─ Base64 encode full payload → `verificationCipher`
└─ Send `verificationCipher` to server (password never sent)
├─ User enters password
├─ Fetch base64 `verificationCipher` from server
├─ Decode and parse:
│ ├─ header (45 bytes)
│ ├─ ciphertext
│ ├─ IV (12 bytes)
│ ├─ salt (16 bytes)
│ └─ HMAC (32 bytes)
├─ Validate:
│ ├─ MAGIC bytes == "NP"
│ ├─ VERSION supported
│ ├─ HEADER hash matches
│ └─ HMAC signature valid
├─ Derive key using KDF_ID (PBKDF2-SHA512 with salt + iterations)
│ ├─ Split into AES-GCM key + HMAC key
├─ Decrypt ciphertext with AES-GCM using IV
├─ Decompress decrypted data using DEFLATE (pako)
├─ Check if plaintext starts with "VERIFY:"
│ ├─ If yes → correct password → unlock vault
│ └─ Else → incorrect password → show error
├─ Call VaultContext.unlockVault(password)
│ ├─ Get masterKey from IndexedDB
│ ├─ Encrypt vault password with AES-GCM + random IV using masterKey
│ ├─ Store encrypted password + IV in memory (React state)
│ └─ Mark vault as unlocked
└─ Call server API `/api/vault/unlock`
└─ Server issues a secure jwt vault session token cookie (30 min expiry)
├─ Vault password stored encrypted in memory (React state)
├─ Encryption uses separate masterKey (from IndexedDB)
└─ Password decrypted on-demand via VaultContext.getVaultPassword()
├─ Retrieve vault password by calling VaultContext.getVaultPassword()
└─ For each PGP key to backup:
├─ Compute hashes and compare with:
│ ├─ IndexedDB PGP key
│ └─ MongoDB PGP key
│ └─ To check the PGP key is already backed up to the MongoDB or not
├─ If not already backed up:
│ ├─ Generate 16-byte random salt
│ ├─ Generate 12-byte random IV
│ ├─ Compress the PGP key with DEFLATE (pako)
│ ├─ Derive 64-byte key from vault password + salt using PBKDF2-SHA512 (1M iterations)
│ │ ├─ First 32 bytes: AES-GCM key
│ │ └─ Next 32 bytes: HMAC-SHA256 key
│ ├─ Encrypt compressed PGP key with AES-GCM + IV
│ ├─ Build 45-byte header:
│ │ ├─ 2B MAGIC ('NP')
│ │ ├─ 1B VERSION
│ │ ├─ 1B PURPOSE
│ │ ├─ 1B KDF_ID (0x01)
│ │ ├─ 1B CIPHER_ID (0x01)
│ │ ├─ 1B FLAGS (0x01 = compressed)
│ │ ├─ 4B ITERATIONS
│ │ ├─ 2B RESERVED
│ │ └─ 32B SHA-256(header)
│ ├─ Compute HMAC-SHA256 over (header + ciphertext + IV + salt)
│ ├─ Concatenate: header + ciphertext + IV + salt + HMAC
│ └─ Base64 encode → encrypted PGP key
└─ Send the encrypted PGP key and its hash to the server and store in the database
├─ Retrieve vault password by calling VaultContext.getVaultPassword()
└─ Retrieve list of encrypted PGP keys from MongoDB
├─ For each encrypted PGP key:
│ ├─ Base64 → rawBuffer
│ ├─ Parse out:
│ │ ├─ header (45 bytes)
│ │ ├─ ciphertext
│ │ ├─ IV (12 bytes)
│ │ ├─ salt (16 bytes)
│ │ └─ HMAC (32 bytes)
│ ├─ Verify:
│ │ ├─ MAGIC == 'NP'
│ │ ├─ VERSION supported
│ │ ├─ header hash matches
│ │ └─ HMAC valid over (header + ciphertext + IV + salt)
│ ├─ Extract ITERATIONS & KDF_ID, derive 64-byte key via PBKDF2-SHA512
│ ├─ Decrypt ciphertext with AES-GCM + IV
│ ├─ Decompress with INFLATE (pako) → PGP key bytes
│ └─ Compute its hash
├─ User clicks "import" on one PGP key
├─ Compare cloud PGP key hash against IndexedDB PGP keys to avoid duplicates
├─ Get masterKey from IndexedDB
├─ Encrypt PGP key with AES-GCM + random IV using masterKey
└─ Store the final AES-GCM-wrapped PGP key (and IV) in IndexedDB
├─ User presses lock vault button or closes tab
└─ VaultContext.lockVault()
├─ Clears encrypted vault password from React state (in-memory)
├─ Calls server API `/api/vault/lock` to revoke jwt vault session token
└─ Sets vault locked flag
| Video 1 | Video 2 |
|---|---|
 |
 |
























This project is licensed under the GPL-3.0 license.
If you have any questions, feel free to reach out:
- GitHub: XBEAST1
- Email: [email protected]
✨ Next PGP simplifies secure messaging. Generate, manage, and encrypt with confidence! ✨