-
Notifications
You must be signed in to change notification settings - Fork 0
JWT
The JWT can be retrieved with Wireshark. When you open Wireshark, start a capture on the active brxxxxx interface with IP addresses starting with 172.16.11. This is the VLAN where the containers communicate. You can quickly find the converstion by applying the following filter:
ip.addr eq 172.16.11.8 and ip.addr eq 172.16.11.11
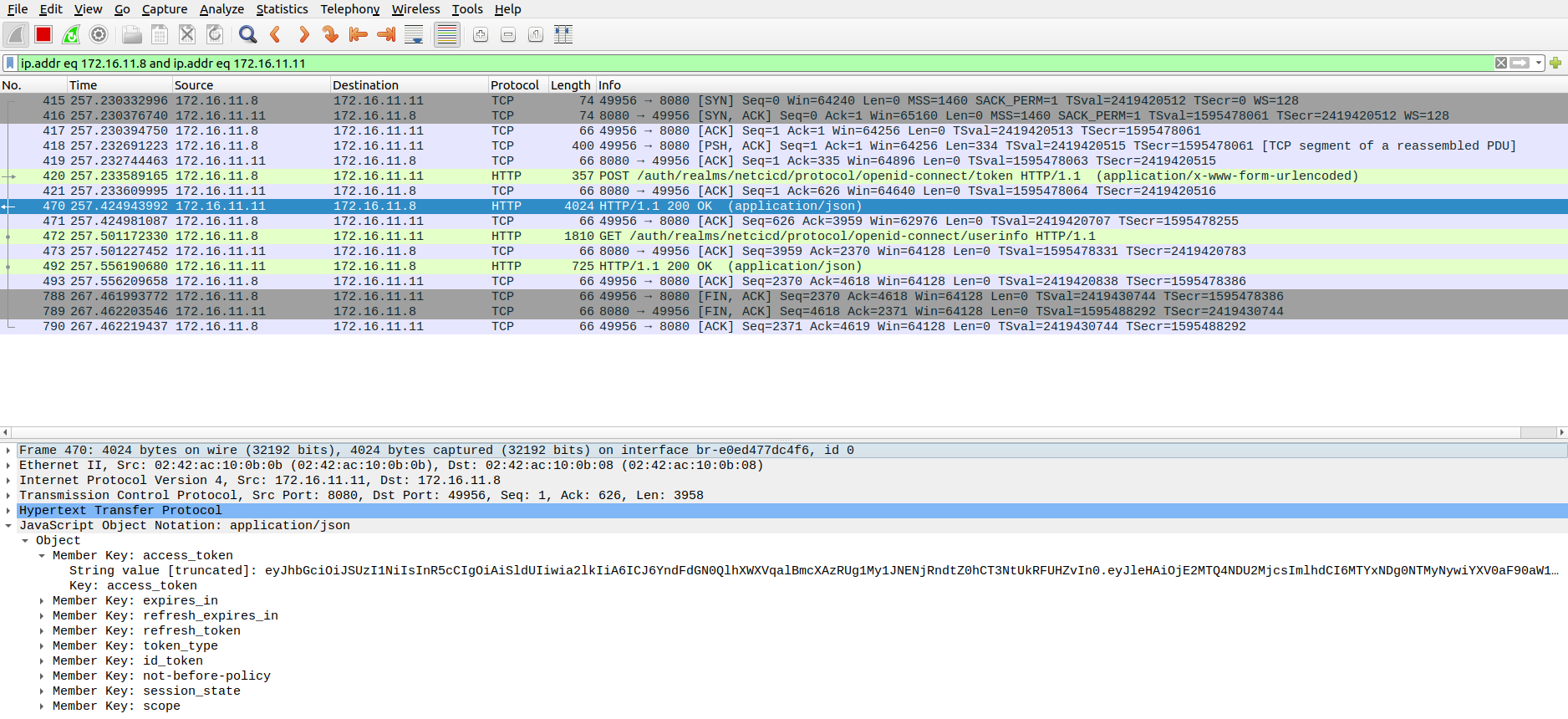
look for the HTTP/1.1 200 OK (application/json) packet in the conversation between Keycloak and Jenkins as shown above.
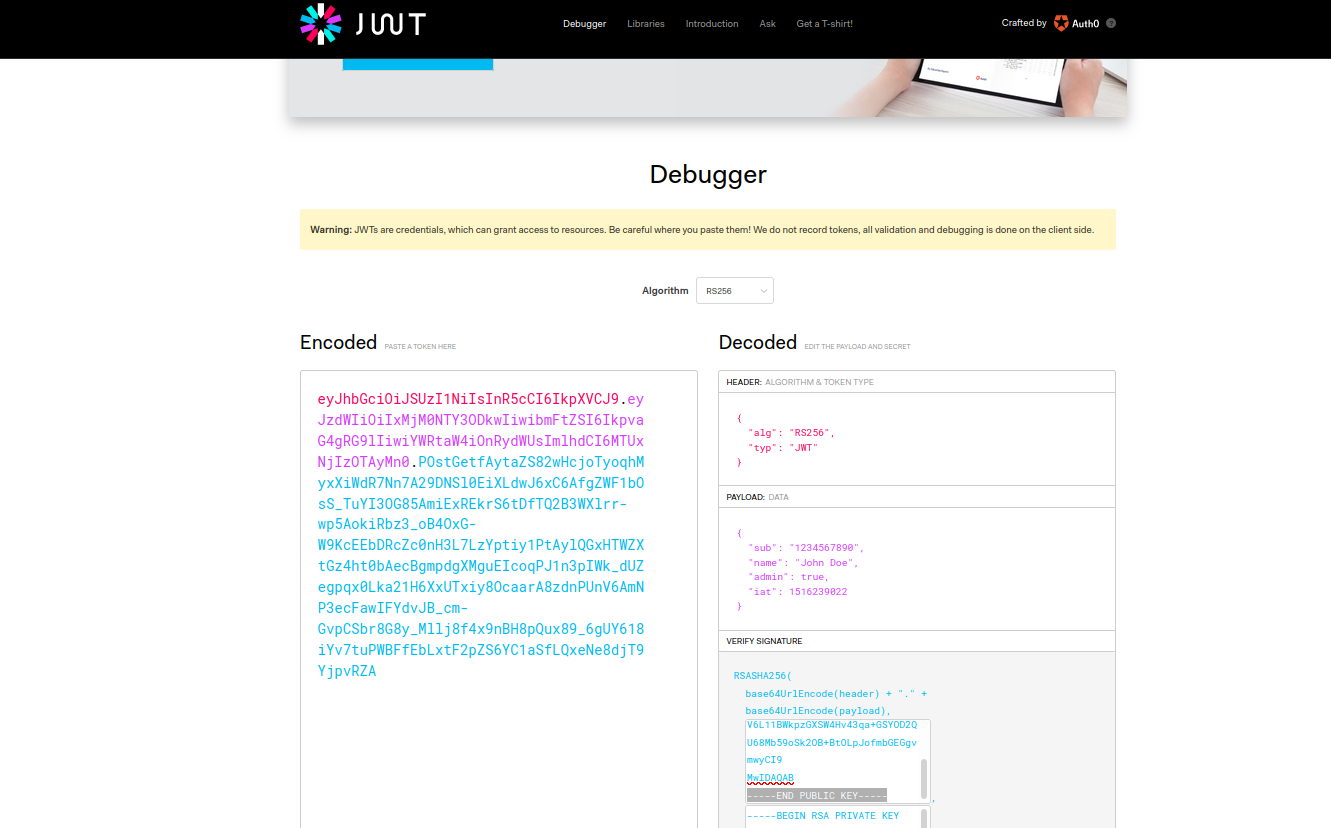
paste the value of the access token into the Encoded window on jwt.io.
To decode the SSL session, you need the RS256 public key for your realm. This can be found inside Keycloak under realm settings as shown below.
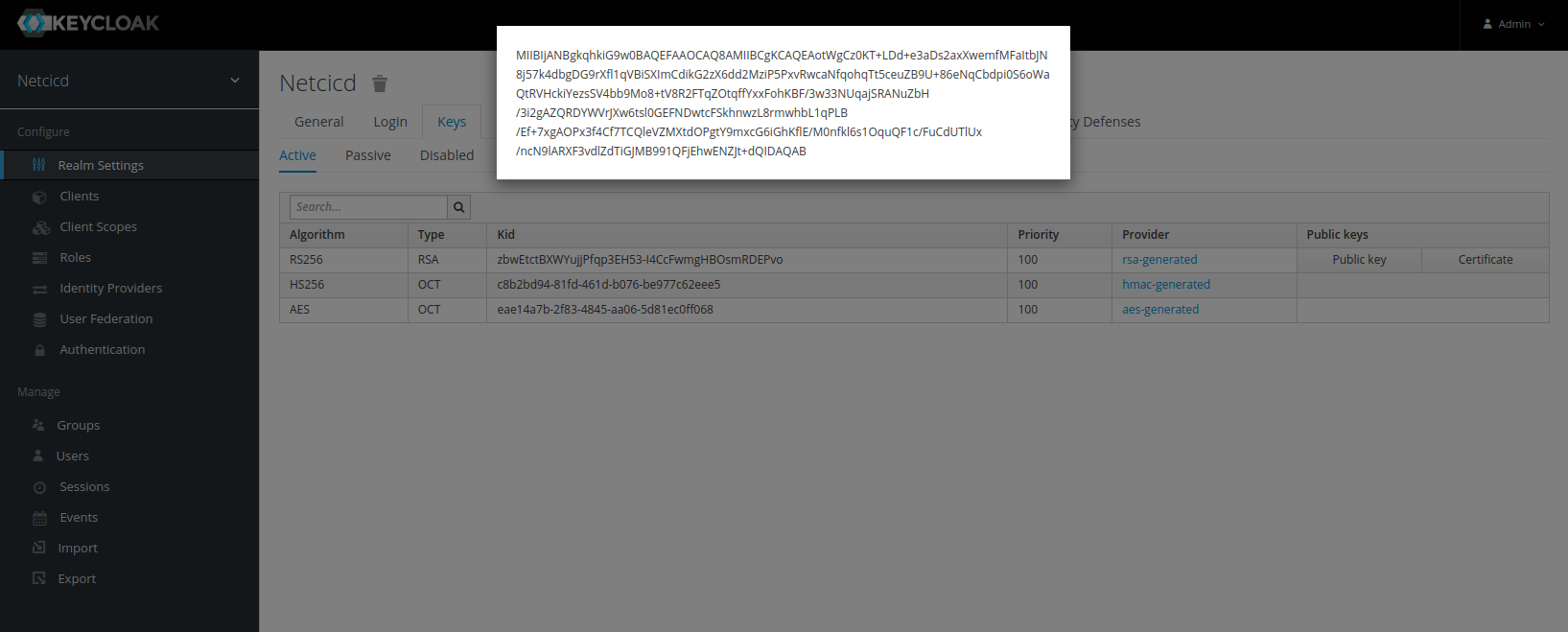
Copy this key, pick the RS256 algorithm in jwt.io and insert the Keycloak public key in the verify signature section after -----BEGIN PUBLIC KEY----- and before -----END PUBLIC KEY-----. The existing key should be replaced.
The Decoded section should show the data, the user info is on the bottom.
Devoteam. Tech for people.