-
Notifications
You must be signed in to change notification settings - Fork 68
Letsencrypt Walkthrough
If I have a registered domain of lophi.us with GoDaddy and I am wanting to access the Kibana service within elk-tls-docker on an Ubuntu droplet on DigitalOcean at https://kibana.lophi.us then I need to point my domain (lophi.us) nameservers to digitalocean by following these instructions from digitalocean.
Next, I need to add A and CNAME records within digitalocean. Yours should look similar to this (but replace it with your domain):
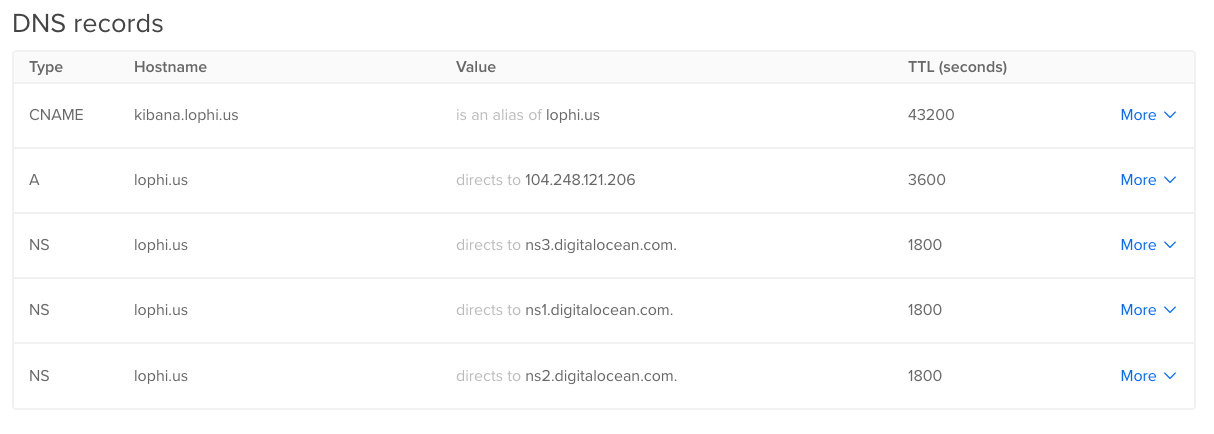
NOTE: This may take several hours to propagate but it will eventually work
Now we can ssh into our digitalocean droplet and begin deploying elk-tls-docker. Please see our deploying and running documentation for more information.
In order to run elk-tls-docker you will need a few pieces of software to be installed:
- Docker
- docker-compose
- git
First you should make sure your system is update to date and then you can install all the prerequisities by copying this and running it on your Ubuntu host.
If you are wanting to access Kibana via a subfolder or a subdomain then you must do the following in one of the two provided sample configurations.
If you are wanting to access Kibana at https://lophi.us/kibana then specify the SUBFOLDER variable in your .env file (without the SUBDOMAIN variable)
You can see the sample subfolder conf file here.
Your .env will look like the following:
ELK_VERSION=7.9.2
ELASTIC_USERNAME="elastic"
ELASTIC_PASSWORD="some_password"
# Configuration Variables
ELASTICSEARCH_HEAP="2g"
LOGSTASH_HEAP="1g"
PACKETBEAT_HEAP="256m"
FILEBEAT_HEAP="256m"
XPACK_ENCRYPTION_KEY="somesuperlongstringlikethisoneMQBbtsynu4bV2uxLy"
# Self signed TLS certificates
CA_PASSWORD="some password"
CA_DAYS=3650
ELASTIC_DIR=/usr/share/elasticsearch
LOGSTASH_DIR=/usr/share/logstash
KIBANA_DIR=/usr/share/kibana
PACKETBEAT_DIR=/usr/share/packetbeat
FILEBEAT_DIR=/usr/share/filebeat
# Letsencrypt certificates
STAGING=false
# swag Configuration
DOMAIN=company.us
SUBFOLDER=kibana
# NOTE: You should have either the SUBDOMAIN or SUBFOLDER variable
[email protected]
TIMEZONE=America/ChicagoIf you are wanting to access Kibana at https://kibana.company.us then you will need to specify the SUBDOMAIN variable in your .env file.
You can see the sample subdomain conf file here.
ELK_VERSION=7.9.2
ELASTIC_USERNAME="elastic"
ELASTIC_PASSWORD="some_password"
# Configuration Variables
ELASTICSEARCH_HEAP="2g"
LOGSTASH_HEAP="1g"
PACKETBEAT_HEAP="256m"
FILEBEAT_HEAP="256m"
XPACK_ENCRYPTION_KEY="somesuperlongstringlikethisoneMQBbtsynu4bV2uxLy"
# Self signed TLS certificates
CA_PASSWORD="some password"
CA_DAYS=3650
ELASTIC_DIR=/usr/share/elasticsearch
LOGSTASH_DIR=/usr/share/logstash
KIBANA_DIR=/usr/share/kibana
PACKETBEAT_DIR=/usr/share/packetbeat
FILEBEAT_DIR=/usr/share/filebeat
# Letsencrypt certificates
STAGING=false
# swag Configuration
DOMAIN=company.us
SUBDOMAIN=kibana
# NOTE: You should have either the SUBDOMAIN or SUBFOLDER variable
[email protected]
TIMEZONE=America/ChicagoIn order to use letsencrypt for certificates, we must have a .env similar to the one below:
ELK_VERSION=7.9.2
ELASTIC_USERNAME="elastic"
ELASTIC_PASSWORD="some_password"
# Configuration Variables
ELASTICSEARCH_HEAP="2g"
LOGSTASH_HEAP="1g"
PACKETBEAT_HEAP="256m"
FILEBEAT_HEAP="256m"
XPACK_ENCRYPTION_KEY="somesuperlongstringlikethisoneMQBbtsynu4bV2uxLy"
# Self signed TLS certificates
CA_PASSWORD="some password"
CA_DAYS=3650
ELASTIC_DIR=/usr/share/elasticsearch
LOGSTASH_DIR=/usr/share/logstash
KIBANA_DIR=/usr/share/kibana
PACKETBEAT_DIR=/usr/share/packetbeat
FILEBEAT_DIR=/usr/share/filebeat
# Letsencrypt certificates
STAGING=false
# swag Configuration
DOMAIN=company.us
SUBDOMAIN=kibana
#SUBFOLDER=notkibana
# NOTE: You should have either the SUBDOMAIN or SUBFOLDER variable
[email protected]
TIMEZONE=America/ChicagoOnce you have your .env file setup properly we must first run the following command. This is a different order than the self-signed certiticate generation that you have already used previously. Please follow the process below to setup certificates properly.
Run the following command once:
NOTE: Make sure you .env has STAGING set to false
docker-compose -f docker-compose.setup.yml run --rm certsThis will generate temporary certificates needed to get elasticsearch running initially while swag generates the letsencrypt certificates.
Now that we have some temporary certificates we need to run the production yaml:
docker-compose -f docker-compose.production.yml upYou will start to see docker downloading the the images (if not already downloaded previously) and you should see output from swag. This output will indicate if swag was able to successfully generate LetsEncrypt certificates or not. This is critical before more moving forward.
You should see similar output to the following (this is truncated):
swag | SUBDOMAINS entered, processing
swag | SUBDOMAINS entered, processing
swag | Sub-domains processed are: -d kibana.lophi.us
swag | E-mail address entered: [email protected]
swag | http validation is selected
swag | Generating new certificate
swag | Saving debug log to /var/log/letsencrypt/letsencrypt.log
swag | Plugins selected: Authenticator standalone, Installer None
swag | Obtaining a new certificate
swag | Performing the following challenges:
swag | http-01 challenge for kibana.lophi.us
swag | Waiting for verification...
swag | Cleaning up challenges
swag | IMPORTANT NOTES:
swag | - Congratulations! Your certificate and chain have been saved at:
swag | /etc/letsencrypt/live/company.us/fullchain.pem
swag | Your key file has been saved at:
swag | /etc/letsencrypt/live/company.us/privkey.pem
swag | Your cert will expire on 2021-02-04. To obtain a new or tweaked
swag | version of this certificate in the future, simply run certbot
swag | again. To non-interactively renew *all* of your certificates, run
swag | "certbot renew"
....
....
swag | [cont-init.d] 60-renew: exited 0.
swag | [cont-init.d] 99-custom-files: executing...
swag | [custom-init] no custom files found exiting...
swag | [cont-init.d] 99-custom-files: exited 0.
swag | [cont-init.d] done.
swag | [services.d] starting services
swag | [services.d] done.
....You can also tell if it was successful since they will be located in the following directory:
ls -al ./swag/keysIf you have ./swag/keys/cert.crt and ./swag/keys/cert.key then it is setup correctly.
Go ahead and run docker-compose down or ctrl + x/c to stop all containers running. You can verify this by running docker ps and no containers should be active/running.
Now that you have LetsEncrypt certificates (e.g. certificate authority / root certificates) we then must run the following command to generate all the necessary certificates for all elk-tls-docker services:
docker-compose -f docker-compose.setup.yml run --rm certsThis will generate the appropriate certificates for all running services. You should see these files in your secrets folder.
Now that you have the correct certificates, we can now run elk-tls-docker and access it via our subdomain.
docker-compose -f docker-compose.production.yml up -dVisit your deployment of elk-tls-docker by visiting https://kibana.company.us (or whatever your domain name is).
You may receive a
502 Bad Gatewayat first but in a few minutes once the Kibana container is fully started you should be redirected to the login page.