-
Notifications
You must be signed in to change notification settings - Fork 793
Monkey Island: Running the monkey on AWS EC2 instances
If your network is deployed on Amazon Web Services (with EC2 instances), and you'd like to run the Infection Monkey in order to test it, this page is for you. You can easily run the monkey on various instances within your network - in a secure fashion, without feeding the Island with any credentials or running shell commands on the machines you want to test.
The results will be exported to AWS security hub automatically, as well. To see more information about that, see the Infection Monkey and AWS Security Hub documentation.
Assuming your network is already set up in AWS EC2, follow these quick steps to get up and running.
In order to run the Monkeys directly from the Monkey Island server, you need to deploy the Monkey Island server to an AWS EC2 instance in the same network which you want to test. For information about deploying the Monkey Island server, see setup documentation.
In order for the Island to successfully view your instances, you'll need to set appropriate IAM roles to your instances. You can read more about IAM roles in Amazon's documentation, but it's not necessary in order to follow this setup.
Go to the AWS IAM roles dashboard and create a new IAM role for EC2. The role will need to have some specific permissions (see Appendix A for that), but you can just create a role with the AmazonEC2RoleforSSM, AWSSecurityHubFullAccess and AmazonSSMFullAccess pre-made permissions. In the end it should like something like this:

For each instance you'd like to access from the island, apply the new IAM role you've just created to the instance. For example:
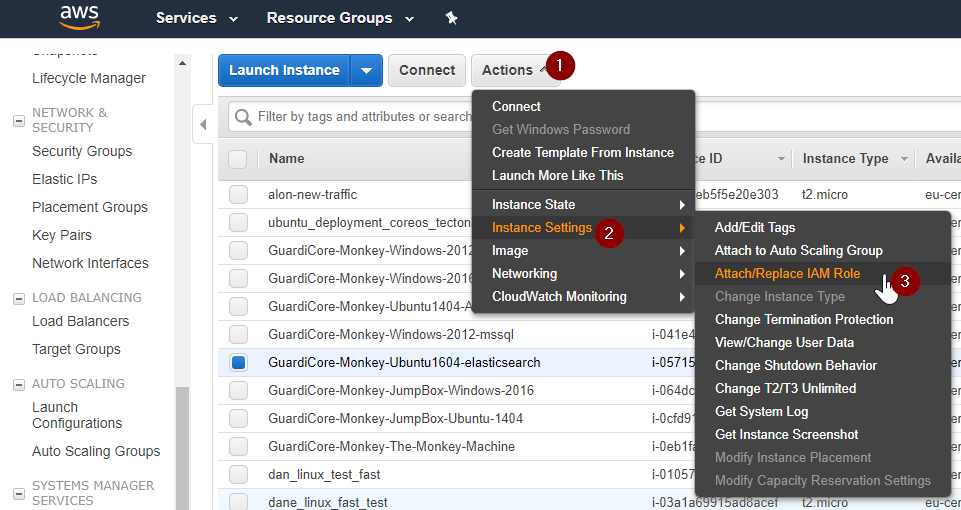
After applying the IAM role you should see this screen:

Note: after setting IAM roles, the roles might take a few minutes (up to 10 minutes sometimes) to effectively kick in. This is how AWS works and is not related to the Monkey implementation. See this StackOverflow thread for more details.
The IAM role will need to have, at least, the following specific permissions:
"ssm:SendCommand""ssm:DescribeInstanceInformation""ssm:GetCommandInvocation"
Note: these can be set on the Monkey Island machine alone, since it's the only one exporting findings to the AWS secutiry hub.
"securityhub:UpdateFindings""securityhub:BatchImportFindings"
If your EC2 instances don't have the SSM agent installed, they will not be able to execute SSM commands, which means you won't see them in the AWS machines table on the monkey island. Generally speaking, most new EC2 instances ought to have SSM pre-installed; The SSM Agent is installed, by default, on Amazon Linux base AMIs dated 2017.09 and later, and on Amazon Linux 2, Ubuntu Server 16.04, and Ubuntu Server 18.04 LTS AMIs.
See Amazon's documentation about working with SSM agents for more details on how to check if you have an SSM agent and how to manually install one if you don't have one.
When you run the monkey island on an AWS instance, the island detects it's running on AWS and present the following option in the "Run Monkey" page, like so:

And then you can choose one of the available instances as "patient zero" like so:
- Click on "Run on AWS"
- Choose the relevant Network Interface
- Select the machines you'd like to run the Monkey on
- Click "Run on Selected Machines", and watch the monkey go! 🐒

- The machines which can use IAM roles and be listed MUST be internet connected (or you can set up a proxy for IAM). This is standard AWS practice and you can read about it (and about how to set up the required proxy machines) in AWS IAM documentation.
- You can see the monkey in the AWS marketplace.
